Using AI for real-time attack simulation at scale (part 3)

This is the final article in this three part series, describing the process we follow at Snode Technologies to go from idea (part 1), through design (part 2) to prototype.

Quick (optional) recap
A quick summary of our collective journey to this point:
Part 1 - Ideation: the journey from problem statement to initial idea generation.
Part 2 - Design: an approach to research, experimentation and solution design.
Part 3 - Prototype: Using hypothesis testing to develop and evolve a prototype.
In the first part we decided to use AI-based attack simulation modelling, to help us prioritise threat and vulnerability response. Attack simulation modelling, using real-time threat and vulnerability data, would identify the most likely risks to be realised.
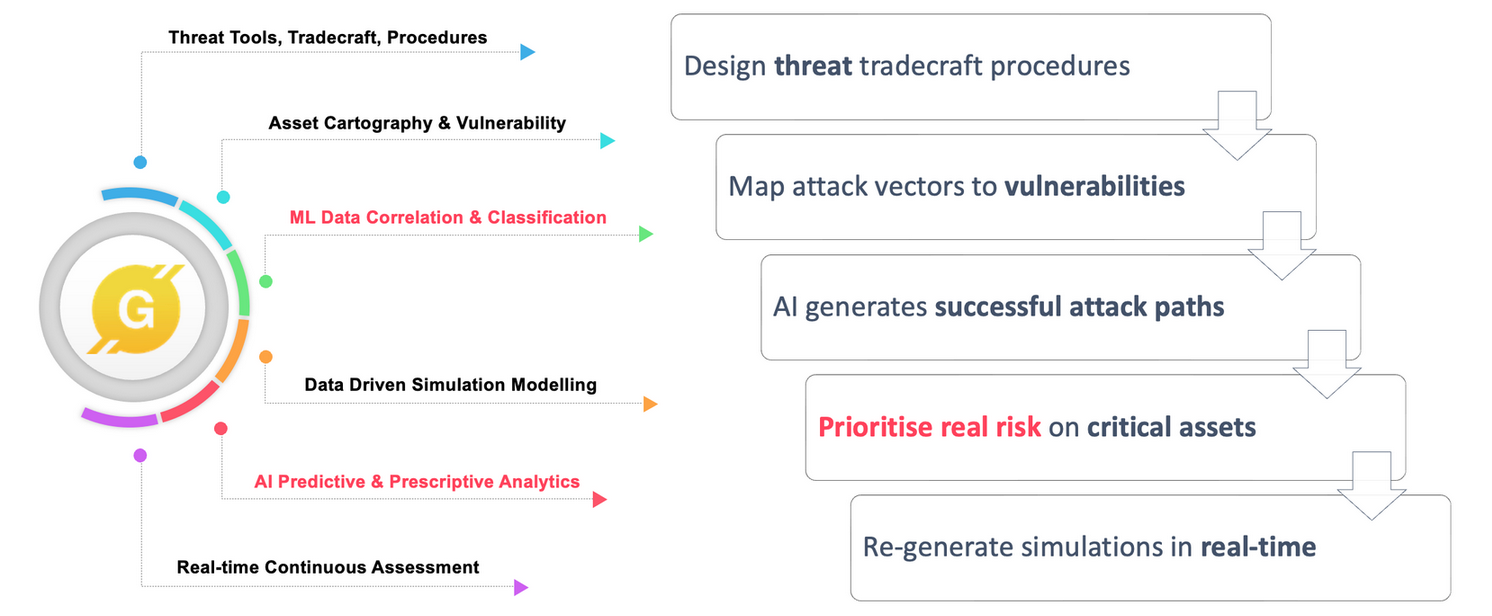
In the second installment we walk you through the design process. We designed high-level entity relationships, context, process and data-flow diagrams to help us unravel the overall approach for prototype development. We also mapped key data sources.
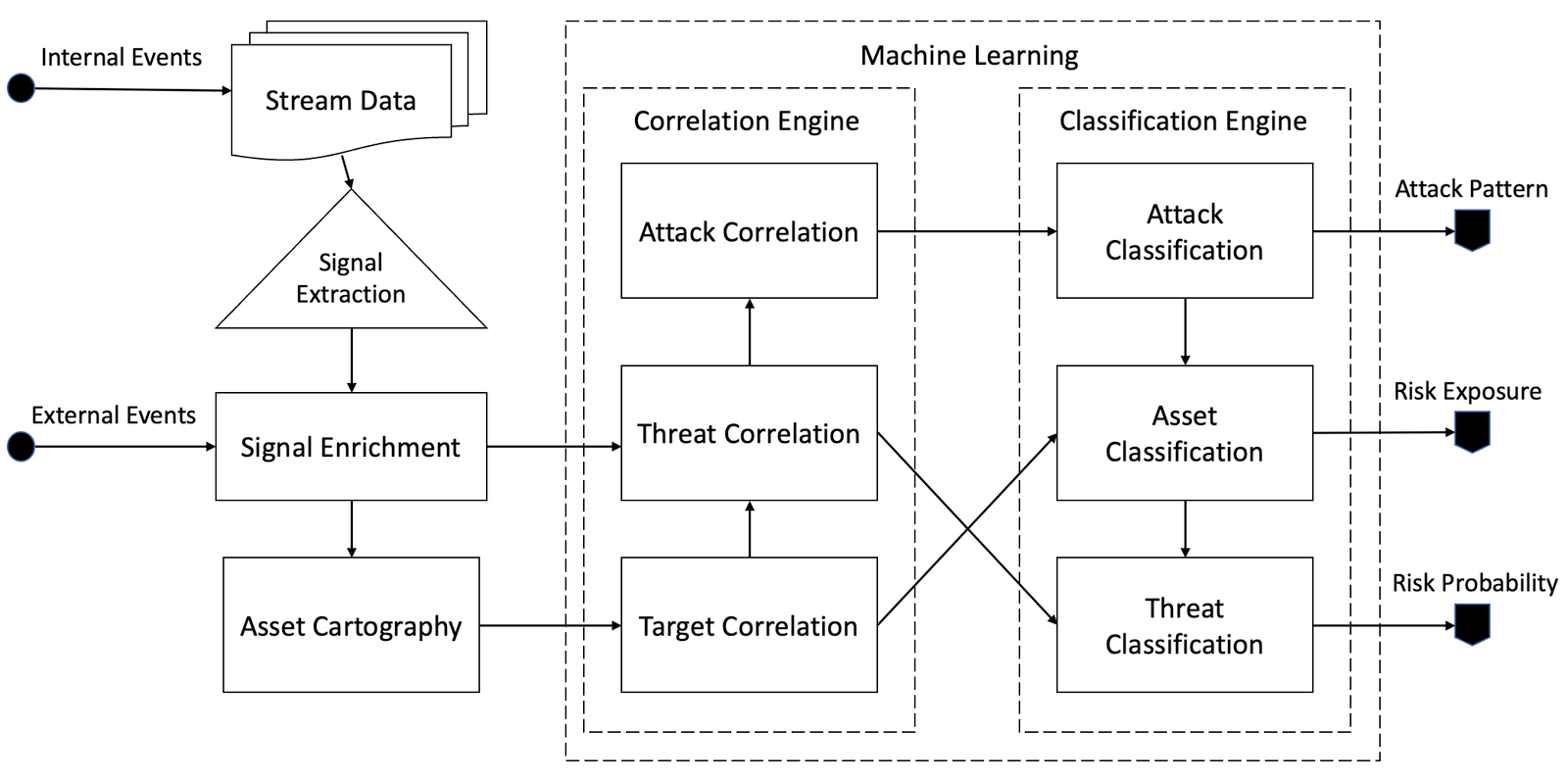
Part 3 - Prototype
The first prototype, as mentioned in part 1, is always an early form of hypothesis test:
- "the first output that Snode's AI-ASM generated (we used Nessus, Nmap, Graphviz and MLpack)".
- "we used Nmap outputs to classify assets (with Bayes) and identify weaknesses (with custom NSE scripts)".
We often test our core assumptions in this way. We focus our work using the simplest forms of (1) data inputs, (2) processing and (3) tooling - to produce an output. This is our version* of an MVP (minimum viable product), but we never release it. We (Snode) only release what you may call MQP (minimum quality product). Our "MQP" approach ensures we reflect our values of innovation and excellence in our client beta releases.
*_I'm not saying Eric Ries implied "low-quality product" when he originally used MVP:

MVP hypothesis testing
Let's use a simple example of news classification to identify vendor specific issues.
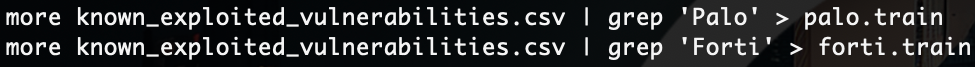
First, we will need training data. We always look for accurate data sources that are well structured for classification. For example, CISA's Known Exploited Vulnerabilities (CSV) dataset would be ideal. Let's use it for our model training in this experiment.
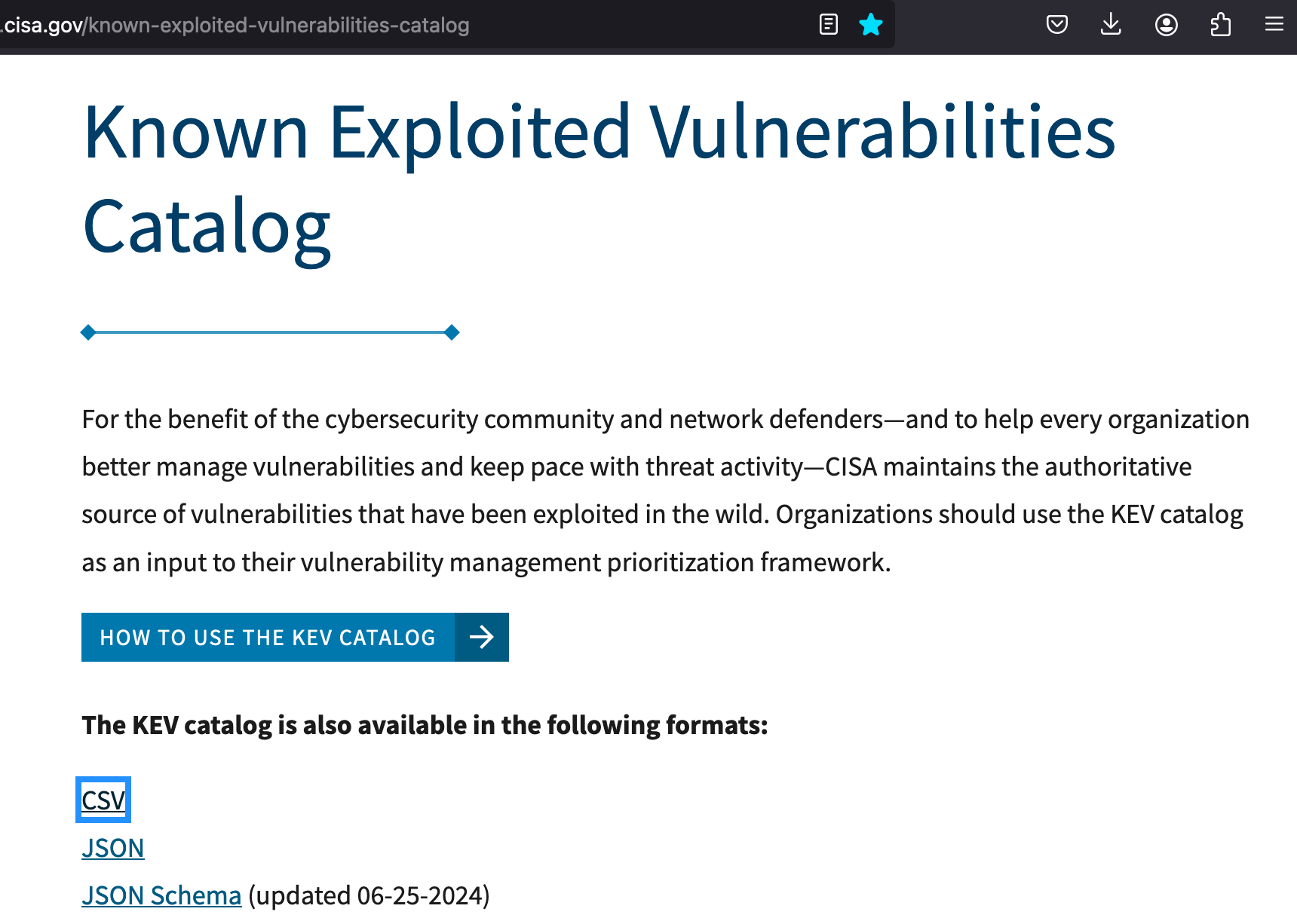
Reviewing the (CSV) data you can easily identify the opportunity to classify by vendor.
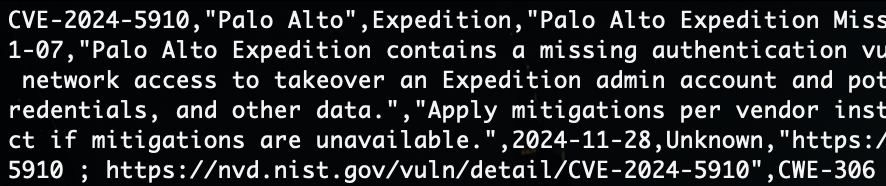
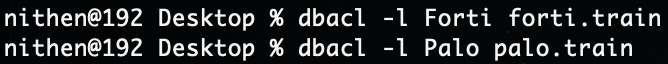
With a lot of attackers targeting internet facing VPN (virtual private network) services, this seemed like a good test case. We just need a Bayes classification tool, like dbacl.
Now let's get some relevant headlines, for two VPN vendors, to do some model testing.
Let's create our training data sets, using the CISA Known Exploited Vulnerabilities CSV.
Now we train classifier models to identify headlines related to Fortinet and Palo Alto.
Lastly, we test (model testing) if the news headlines are correctly classified by vendor.
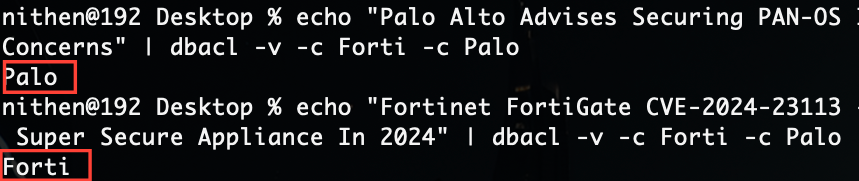
Now we just need to perform the same for every software and network vendor ever!!! Which means we solved the initial problem - we simply need to SCALE our solution. ;)
I'm only half joking,... having a solution that doesn't SCALE (yet) is a great position!
We just moved from a "known-unknown" to a "known-known". So, in summary:
- We always start with the "known-unknowns" and solve the problem statement.
- We build "known-knowns", like interfaces, last - because we know how to do it.
- We start with the simplest form of (1) input, (2) process, (3) code; and SCALE it.
MQP releasing the beta
The Beta is always a combination of solving the problem and a great user experience.
In the case of the attack simulation we went from the flat monochrome diagram to a fully interactive real-time network visualisation. This allowed the user to visually digest the information and glean insights faster. This is achieved without cognitive overload from multiple bar graphs, pie charts and traffic light risk ratings (as shown below):
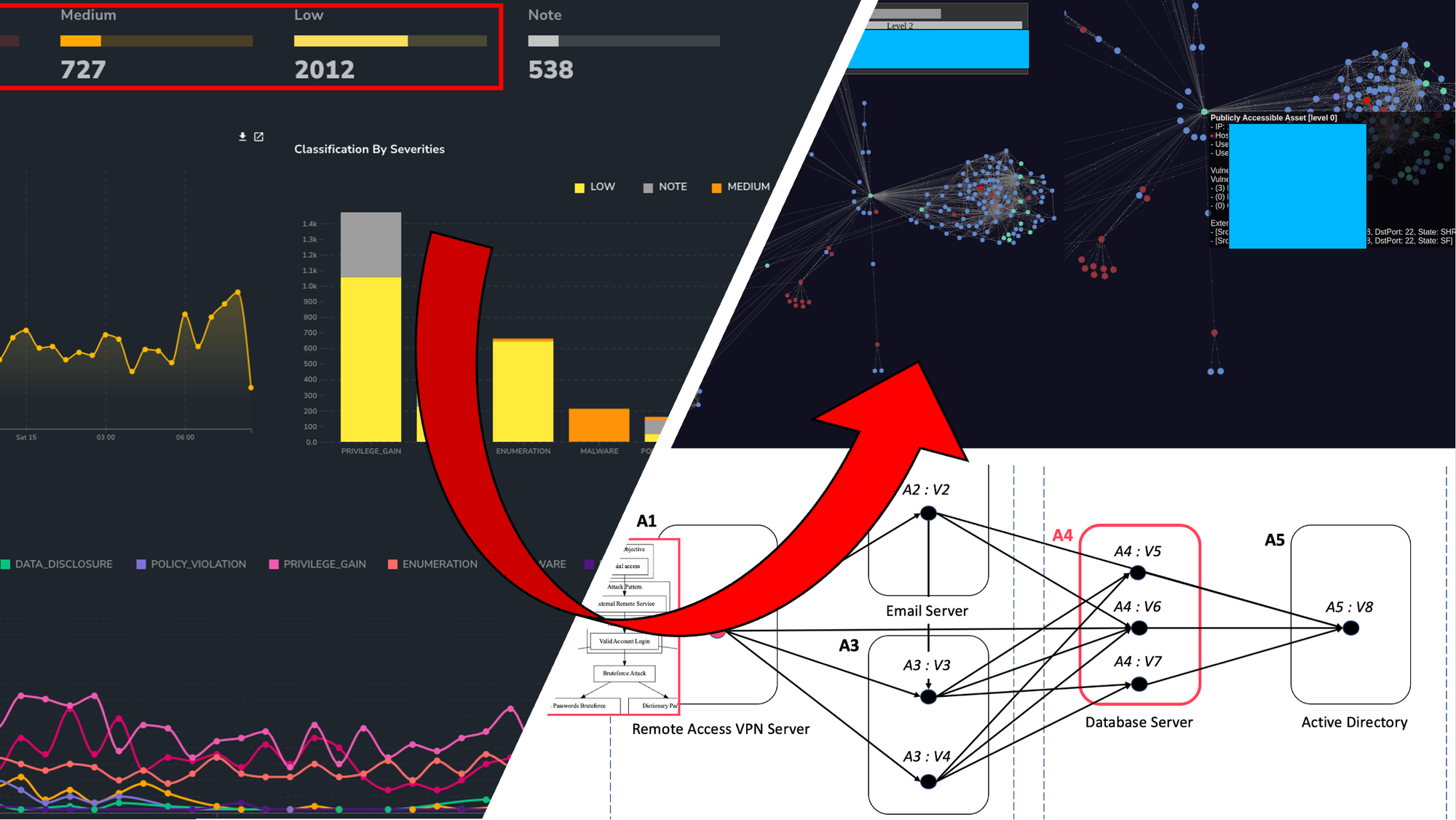
Conclusion
The platform described made it into production. At the time of writing there are several clients running this new technology. I hope this helps and inspires your next innovation.
I'll produce a video and article showcasing the new AI-platform - subscribe to get it.
References

