Using AI for real-time attack simulation at scale (part 2)

This is the second article in a three part series, describing the process we follow at Snode Technologies to go from initial idea (part 1) to functional prototype (part 3).
Quick recap (part 1)
In the first part we decided to use AI-based attack simulation modelling, to help us prioritise threat and vulnerability response. Attack simulation modelling, using real-time threat and vulnerability data, would identify the most likely risks to be realised.
Part 2 - Design
Design philosophy
Our approach to product innovation is guided by our design philosophy.
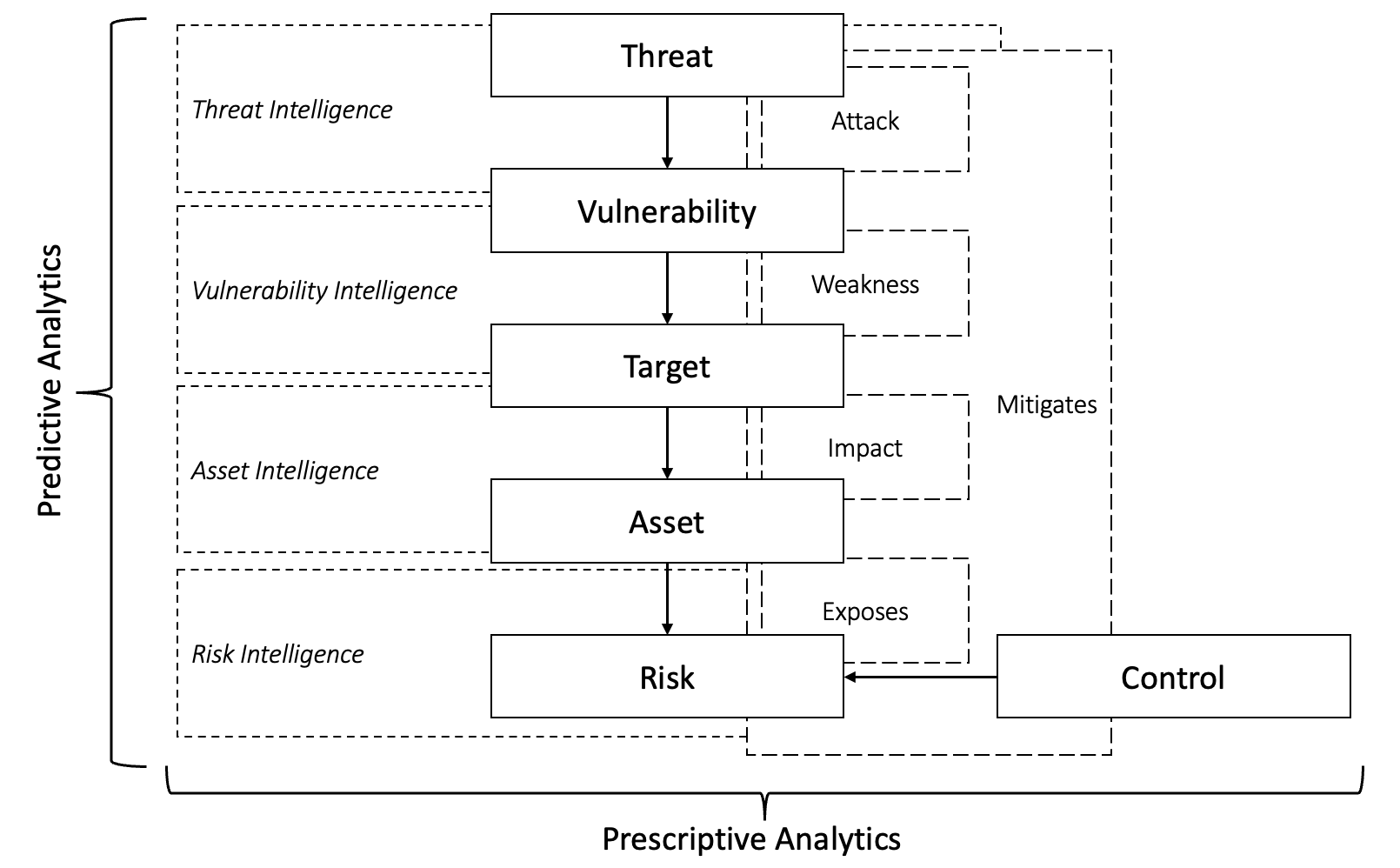
High-level overview
At a macroscopic (conceptual) level, this would be the basic system representation.
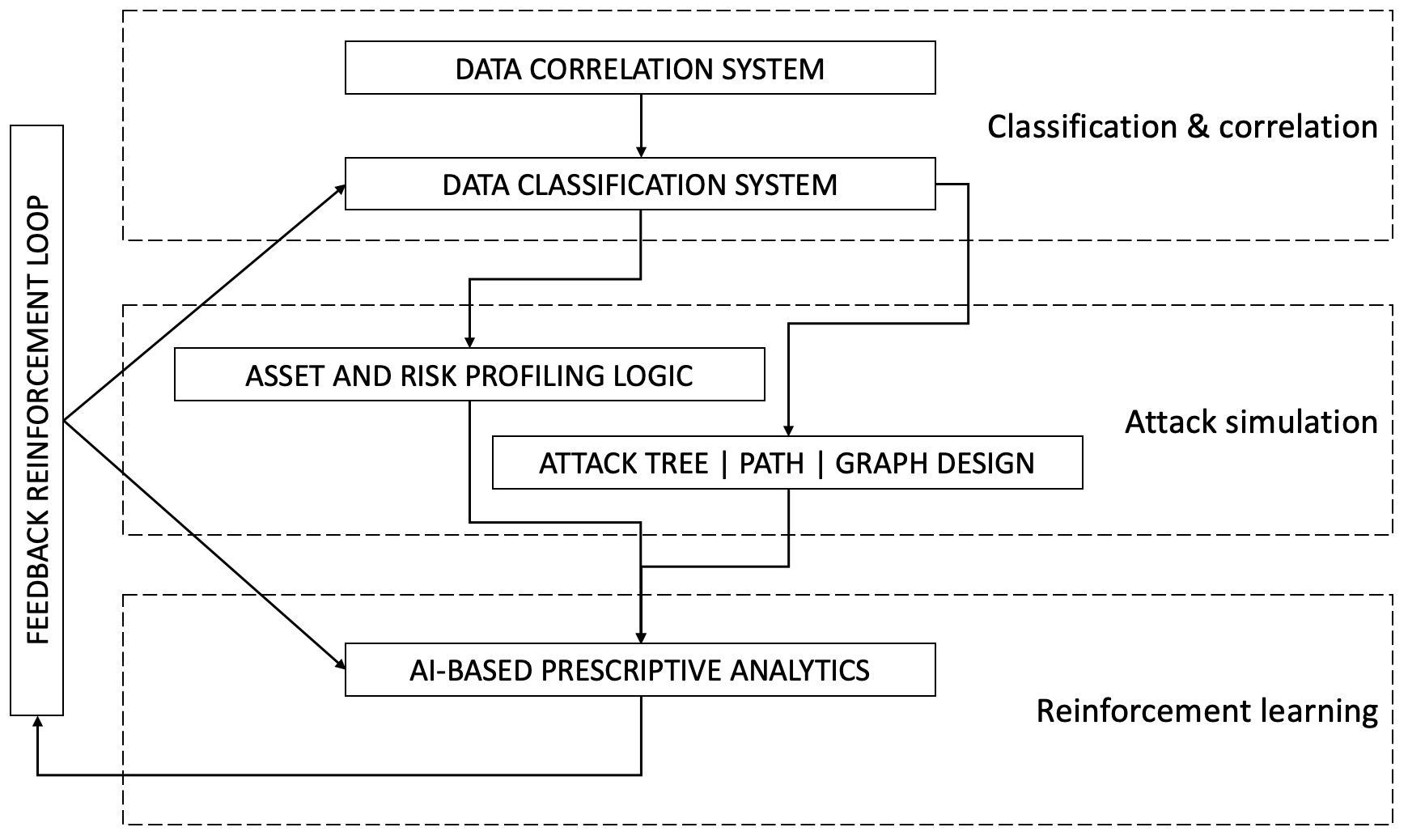
Sub-component overview
We split the system (above) into three sub-components (for detailed design):
- Classification and correlation.
- Attack simulation modelling.
- Supervised ML (re)-training.
Context Diagram
Always start with a context diagram. This shows all external (machine and human) interfaces, inputs and outputs. These will correlate to entry (inputs) and exit (output) points (terminators) on your DFDs (data flow diagrams) that follow.
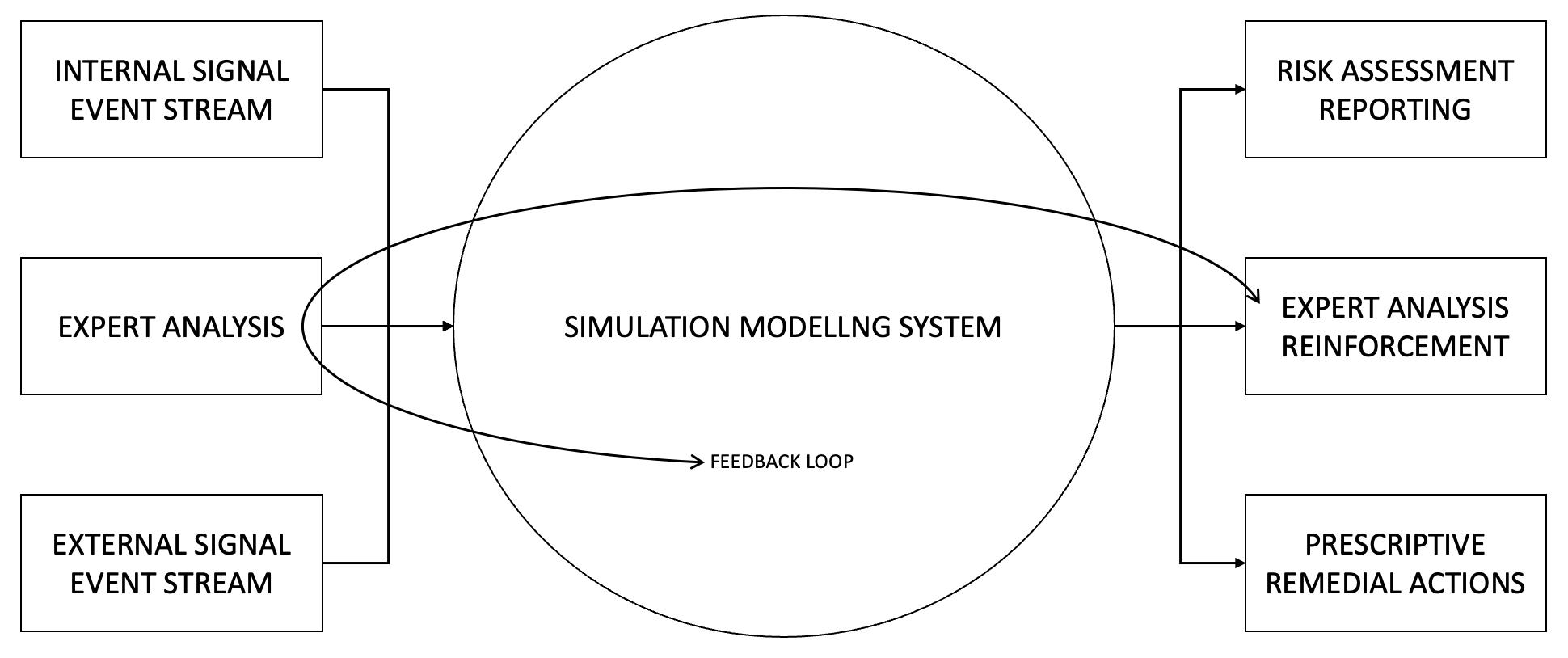
Data Flow Diagram (DFD)
Keep in mind - this is a rough design to guide development - the working prototype may not align to this process flow. That said, this is the original DFD we designed.
To better understand the flow, I'm going to draw a simple real-world parallel. Let's take the attack on the VPN example from our initial blog post (part 1).
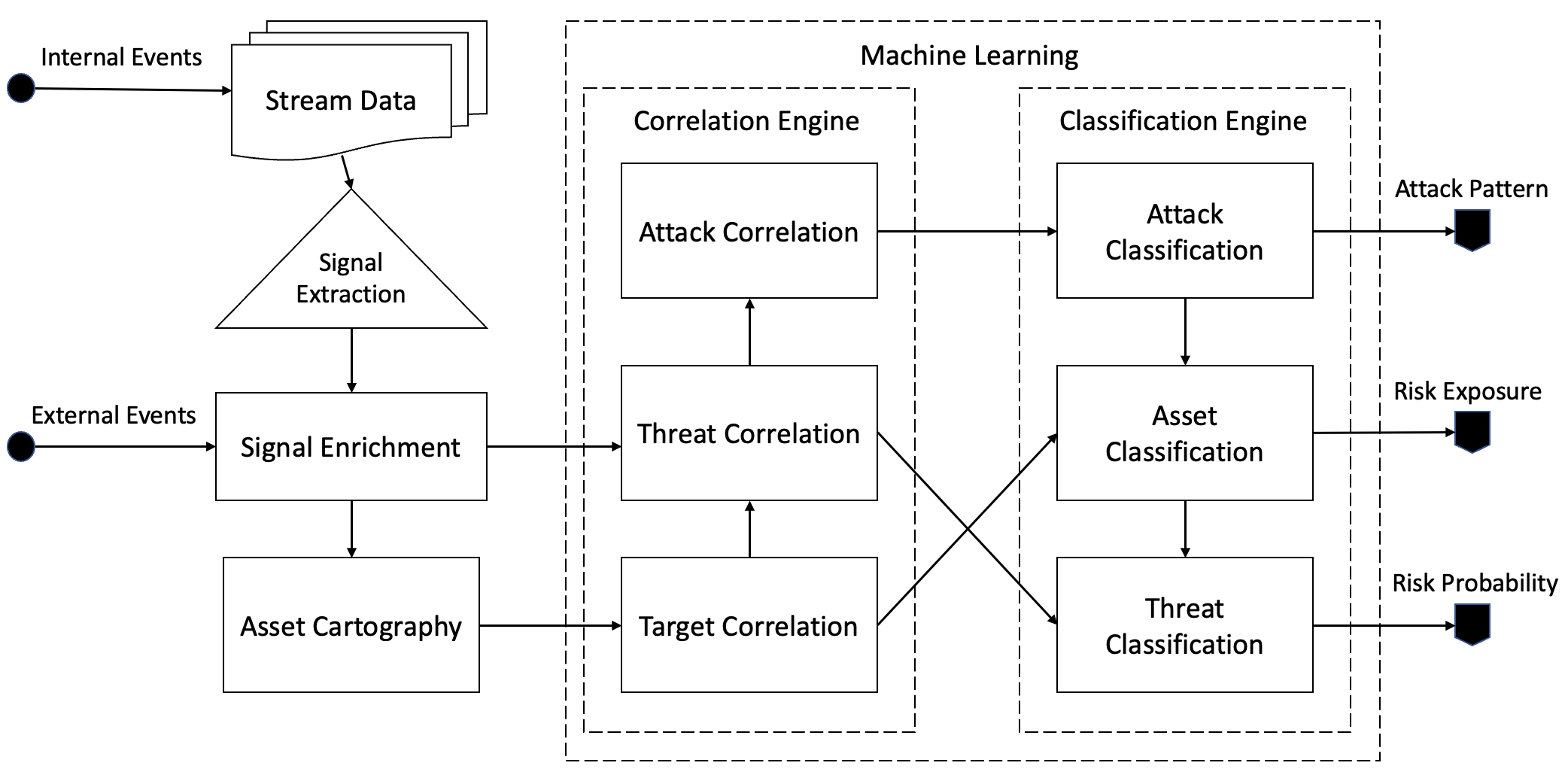
The sub-system will pick up an IoA (indicator of attack), this input will be an "internal event". This will be enriched with threat intelligence, described as an "external event". Together with the necessary asset intelligence (e.g., ML classification determines it is a VPN); we classified this attack pattern as an attempt to gain unauthorised access to a remote access gateway (ATT&CK TA0001, "initial access").
Taking the example further, if we identified the absence of a mitigating control (such as MFA, mitigating TA1078) - OR - the presence of an unauthenticated RCE (remote code execution) vulnerability (TA1190); the probability would be deemed "highly likely".
Thereafter we would try to detect and correlate additional patterns of behaviour (the following stages in the attack chain). We would cross-reference threat intelligence for tools, trade craft and procedures (TTPs) - which may follow. For example, lateral movement (TA0008) using legitimate remote services (e.g., SMB) to logon with a valid account. Such malicious activities, appearing legitimate, may go unnoticed. If network propagation is indeed possible, the risk is mapped to all critical assets that may be affected. This will raise the severity of the vulnerability allowing for the initial access.
Therefore, not all "critical" vulnerabilities are equal. This empowers prioritisation allowing for data-driven, risk-based remediation and proactive threat response.
Data sources
These are the data sources which would be relevant (to the example above):
- Threat monitoring (e.g., IDS event) feed.
- Threat intelligence (e.g., IoC data) feed.
- Vulnerability detection (scan result) feed.
- Asset (ML) profiling using network data.
- Attack & threat classification (ML-model).
Conclusion
There are two more sub-components. However, this illustrates how systems design guides (prototype) development. Today, with Generative AI, design is all you need to build an innovative software solution.
Next blog series, I'll post on how to use Gen-AI to rapidly develop scripts for detection; based on new emerging vulnerability and threat intelligence (subscribe to be notified).
Disclaimer - again, if I got something wrong,...

Tooling References
Although this post is all about design, I thought these platforms were relevant:
Snort - yes, still a single thread; and still the best intrusion detection system:

OpenVAS - open source vulnerability scanner - well maintained and reliable:

OpenCTI - threat intelligence platform - I used it a long time ago and I liked it:

