Twins in Space - AI & DT for space cyber defence (part 1)

Cyber adversaries are expanding their reach beyond terrestrial networks. Recently, incidents targeting satellite and space systems have demonstrated the potential for adversarial manipulation, operational disruption and sensitive data breaches. Such threats have significant implications for commercial enterprise and national security.
Precursor to my Counterspace talk at BSides Joburg 2025: https://bsidesjoburg.co.za/

Key Takeaways
- Understand the space domain, systems and counterspace.
- Identify how it may exist or emerge in your threat landscape.
- Map potential opportunities to innovate in your organisation.
Series Overview
- As an introduction, we will define various orbits and forms of counterspace.
- Discuss why cyber counterspace is important to all countries, including SA.
- We will breakdown basic space systems, including terrestrial components.
- Introduce a list of relevant frameworks developed for space cybersecurity.
- Get into the challenges, and opportunities, specific to cyber counterspace.
- Solutions to prevent counterspace attacks and improve space cybersecurity.
- Discuss what we are doing at Snode Technologies to innovate in this “space”.
Part 1 - Content
In this first article we introduce key terminology referenced in future installments.
- Twins in Space - Introduction
- What is Counterspace?
- What is a Space System?
- Where is Space exactly?
- Digital Twin (DT)
- Fully Homomorphic Encryption (FHE)
- Assured Micropatching (AMP)
- AI-based Threat Detection (Cyber AI)
Twins in Space - Introduction
Innovative technologies, such as Fully Homomorphic Encryption (FHE), AI-based threat detection and DT simulation, are revolutionizing space cybersecurity. Drawing from my experience in the design and development of Snode's Cyber-AI platform (Guardian), a globally patented real-time detection and response system, let us explore how cutting-edge security strategies like these help mitigate Cyber Counterspace threat exposures.

What is Counterspace?
Counterspace - deters, disrupts, denies, degrades or destroys space systems.
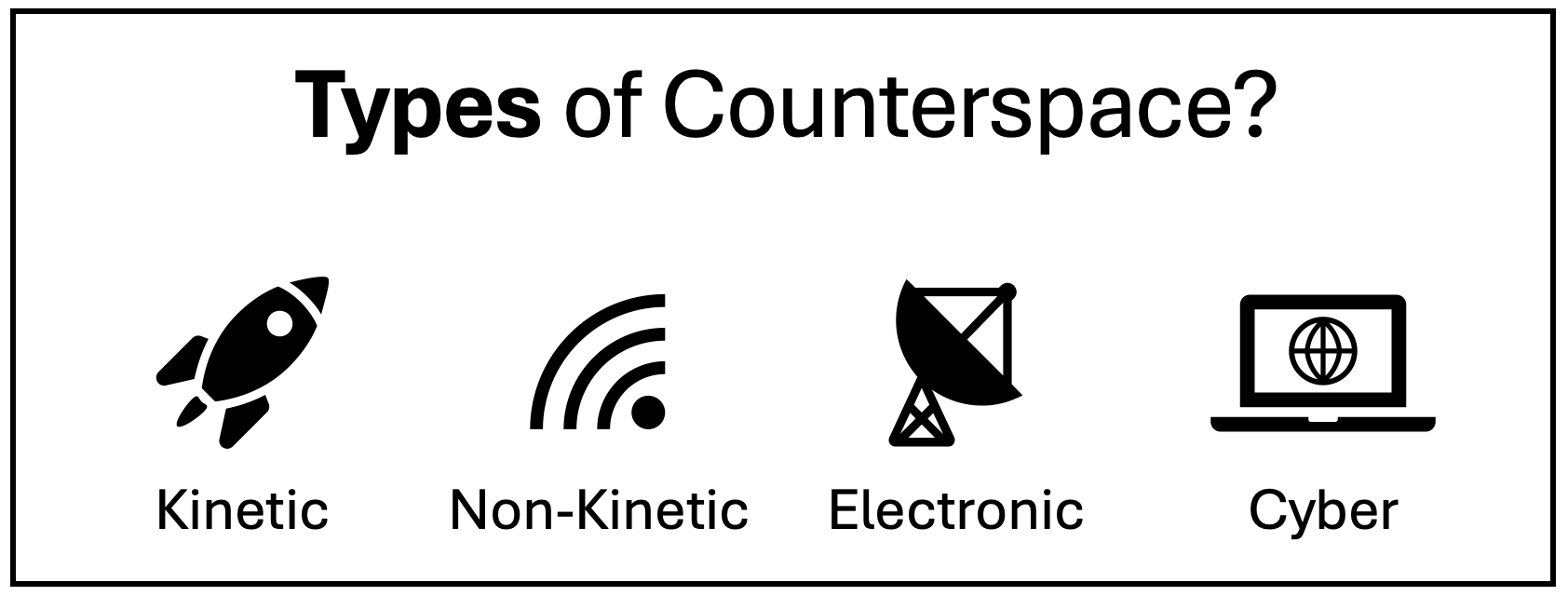
There are four main categories of Counterspace activity:
- Kinetic - like a missile (destructive projectile stuff);
- Non-kinetic - not a missile (e.g., information warfare);
- Electronic - like an EMP (electromagnetic pulse); &
- Cyber - software exploit against space infrastructure.
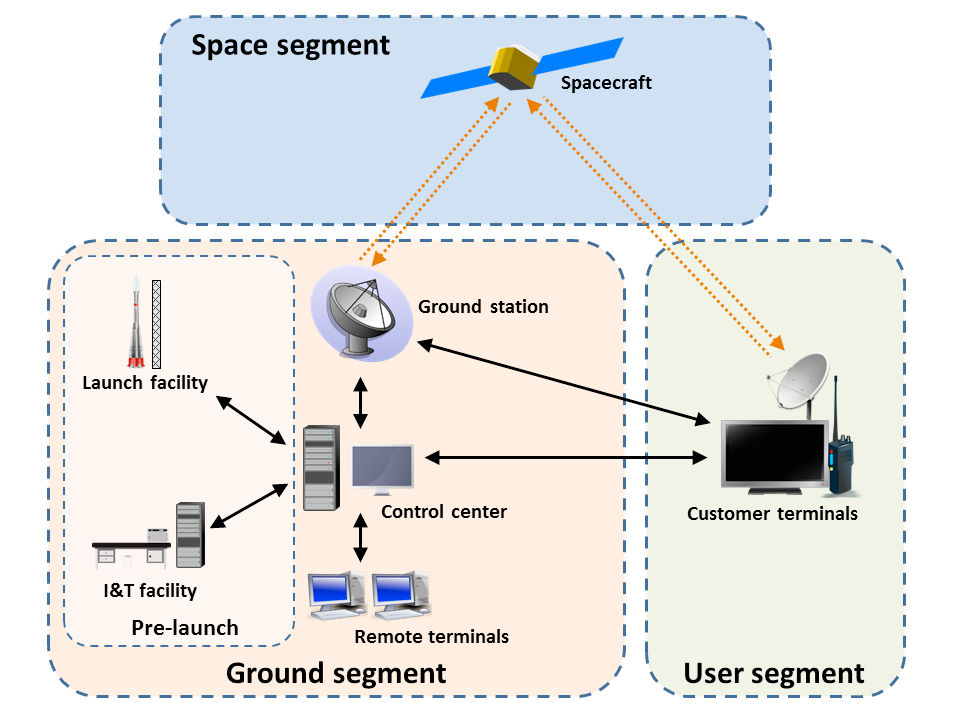
What is a Space System?
A basic space system comprises of a space and terrestrial ground and user segment.
Where is Space exactly?
The theater of engagement exists across multiple orbits, including the following:
- LEO - low earth orbit;
- MEO - medium earth orbit;
- GEO - geostationary earth orbit;
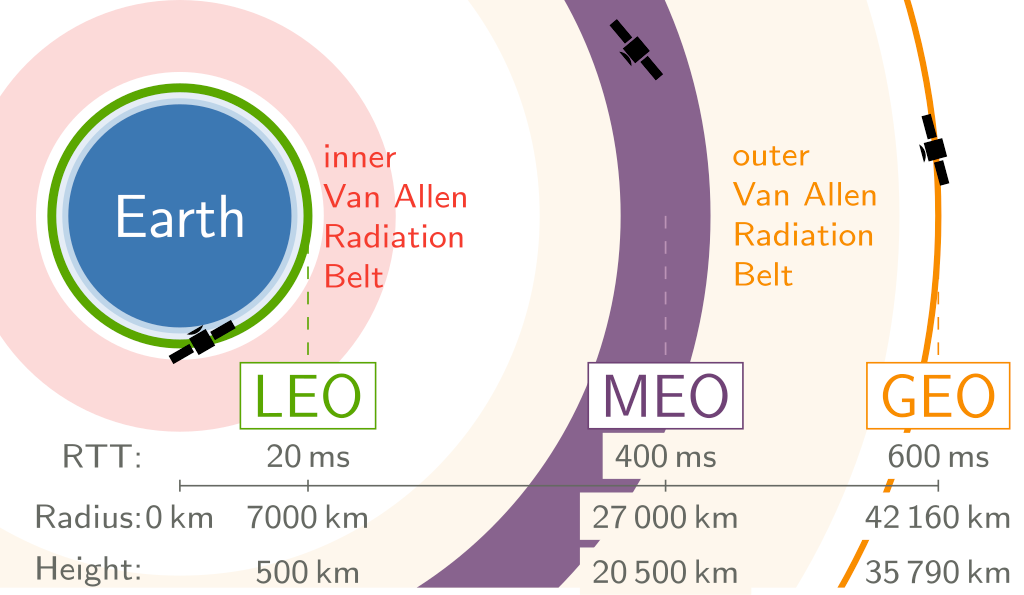
So, where does space start? Well, LEO starts at 180 KM from the surface of earth.

Digital Twin (DT)
A Digital Twin is a digital “mirror copy” counterpart of a physical (or digital) environment. It incorporates all changes, in real-time, and provides a digital copy of all attributes (over a time dimension). The concept of developing a “digital twin” date back to the 1960s at NASA (National Aeronautics and Space Administration). The term “Digital Twin” was first introduced by Dr Michael Grieves, an advisor to NASA, in 2002.
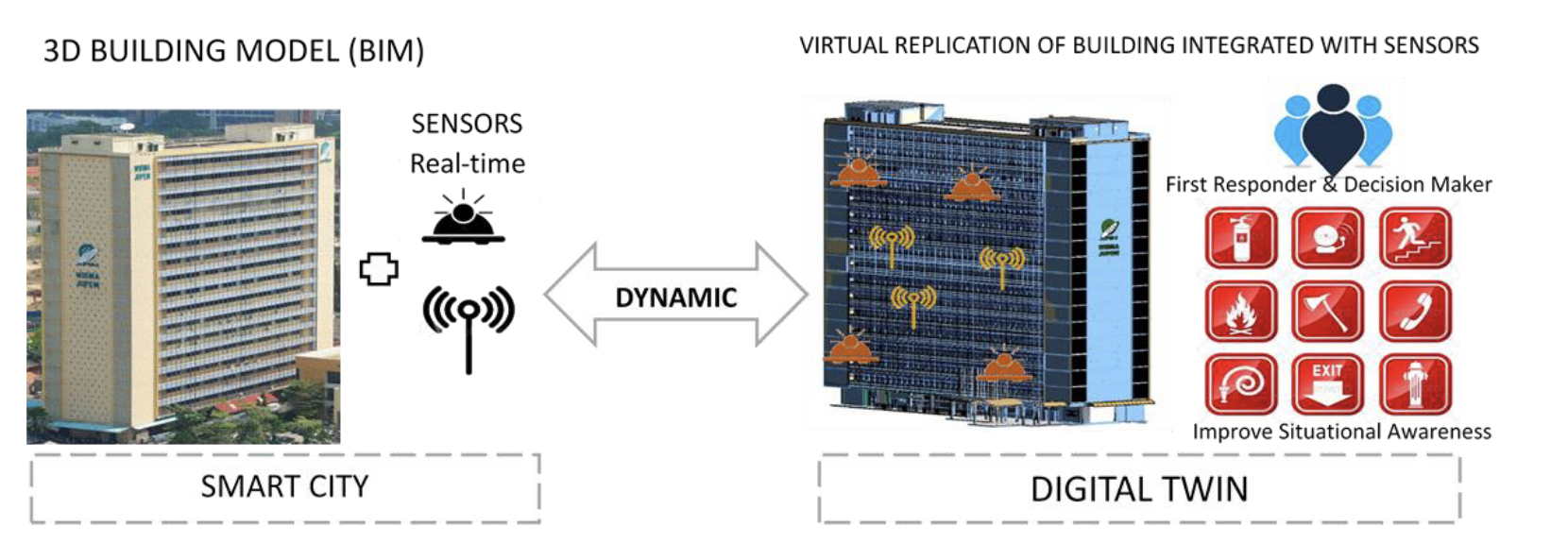
Digital Twin has bi-directional communication between the original and mirror. So interestingly, these are two concepts that are often confused with Digital Twin:
- Digital model - no communication flow. &
- Digital shadow - one way communication.

So, running a Formula 1 car in a wind tunnel simulation is more comparable to a digital model. While Snode's AI-based attack simulation is more aligned to a digital shadow.
Typical types of Digital Twin include:
- Monitoring;
- Predictive;
- Prescriptive;
- Autonomous;
- Imaginary; &
- Re-collective.

Fully Homomorphic Encryption (FHE)
So, in general, we (1) process, (2) transmit and (3) store data. Now, when you think of data encryption during transmission (1) - you may think of SSL (secure sockets layer). Similarly, if you think "encryption at rest" (3) - you may think of hard drive encryption.
What about encryption during processing? Well that's where we look to decrypt and then process (3). Now, you think to yourself - but what if it was possible to process encrypted data - that's way more secure right? Correct, that's what we call FHE baby!
FHE is also known as the "holy grail" of encryption. Here is a cool paper for OpenFHE.

Assured Micropatching (AMP)
Legacy binaries, some of which have no associated source code, need to be assessed and patched for vulnerabilities. Micropatching is a mechanism for altering a compiled binary in a way the remediates or mitigates a vulnerability. This approach will identify, modify and remediate vulnerable binaries without adversely affecting the availability or functionality of the system.
Check out SHIVA from the "ELFMaster" website: https://arcana-research.io/
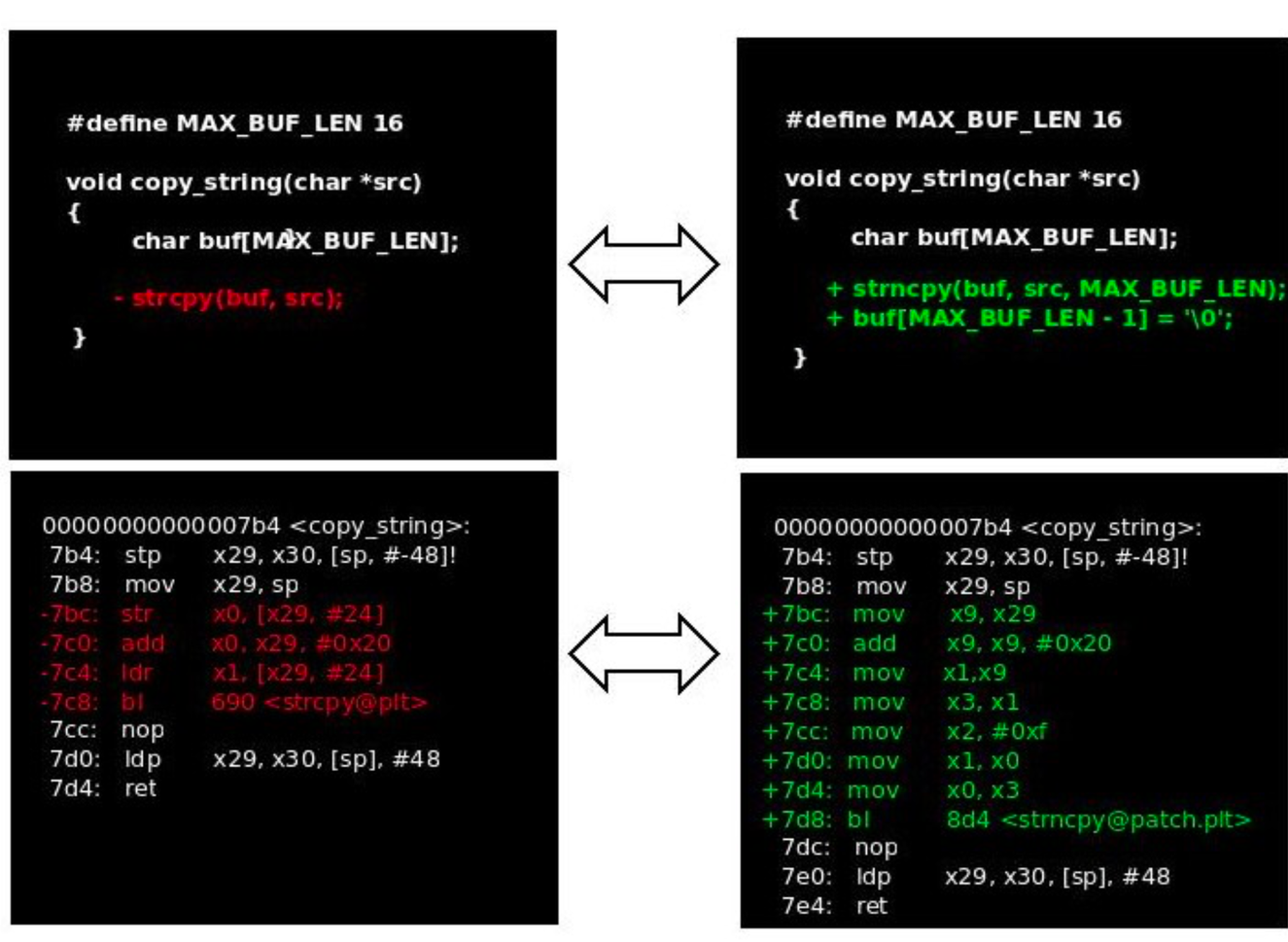
AI-based threat detection (Cyber AI)
This is a broad topic, since there is a range of AI-based approaches to threat detection.
However, for the scope of this article, lets focus our attention on the most prevalent:
- The most common use case is machine learning (ML) for anomaly detection. This is both supervised and unsupervised learning ML algorithms that detect anomalies.
- Deep Learning (along with ML) for cybersecurity classification. This is one of my favourites, especially Bayesian Classification, which is used in your SPAM filter. Deep Learning can help classify malware and is also used in behavioural analytics.
- Reinforcement Learning which is used for adaptive defence. We use this in Snode's SOC for incident response automation, but its also used for prescriptive analytics.
If you keen to see and example of how we implement this at Snode check out this post:

In the example (above), we split our AI-based solution into three sub-components:
- Classification and correlation.
- Attack simulation modelling.
- Supervised ML (re)-training.
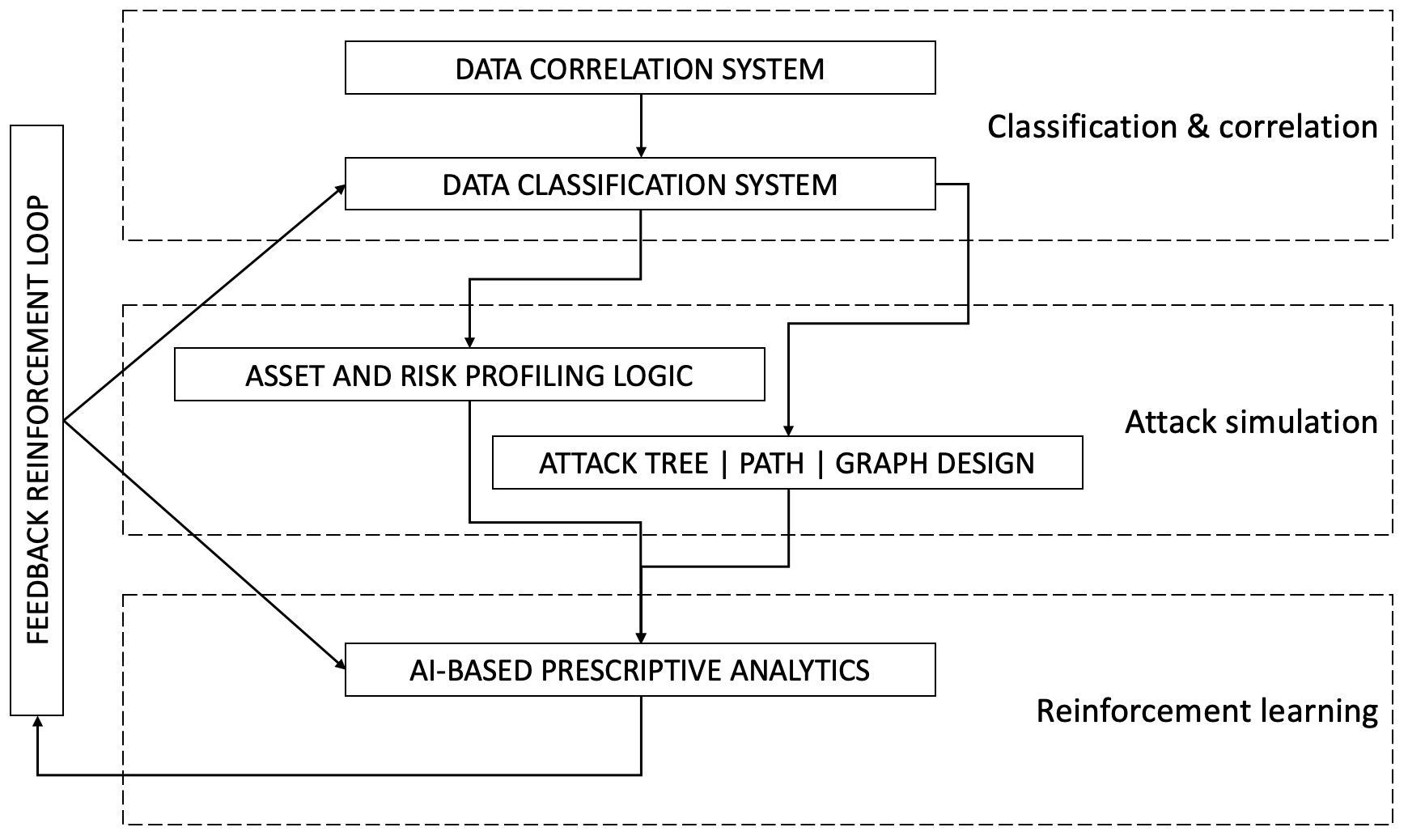
A detailed explanation of Cyber AI from ideation to prototype - and now in production.
Conclusion
In part 2, we will unpack the current challenges with regards to Cyber Counterspace.
Subscribe to be notified and as always, if I got anything wrong,...

References
The following websites serve as appropriate references for additional detail: