Getting the security basics right is hard, but it remains essential

A few weeks ago I was invited by Mancosa to present to their staff and students.

The topic: the importance of building a strong security culture.
3 core messages I wanted to communicate:
- How most cyberattack victims, failed to get the basics right;
- Why victims then respond with increased security spend; &
- Burn millions on new products and services, with little return.
What does this have to do with culture? I want to highlight how talent, design, testing and training are the highest yielding, yet most overlooked, defence tools in any arsenal.
Failing to get the basics right?
In most of the incidents we were called on to respond to (either as Snode or through a partnership) the initial compromise is a resultant of a basic control failure or oversight.
The following high-profile breach (covered in the media) illustrates this point nicely:

The cyber-attacker claimed: "They were using the word ‘password’ as their password.”
While this is a progressive organisation, with excellent leadership, this incident is a pattern we see in most cyberattacks we have responded to globally. Getting the security basics right, is hard, but it remains essential - if you want a resilient posture.

Here are five common (initial) attack vectors Snode sees when called in to respond:
- Unauthorised VPN (virtual private network) access using a compromised account.
- Unauthorised RDP (remote desktop protocol) access using a compromised account.
- Unauthorised access exploiting a known RCE (remote code execution) vulnerability.
- Unauthorised access to an internet-facing database using a compromised account.
- Unauthorised access using a social engineering (e.g., phishing email) attack vector.
Unsurprisingly, this correlates to the most prevalent attack vectors seen by other firms.
For example, let's look at the top five human-operated ransomware group kill-chains, specifically for initial access (taken from SentinelOne's Watchtower Report for 2023):
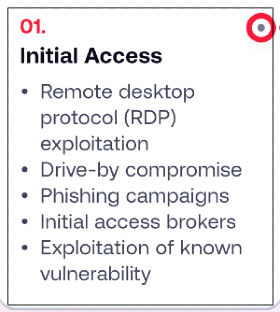
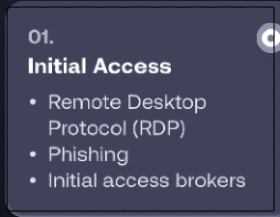
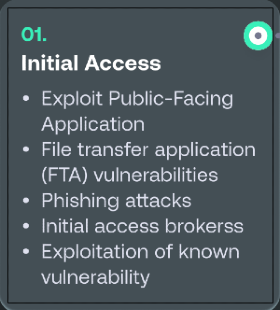
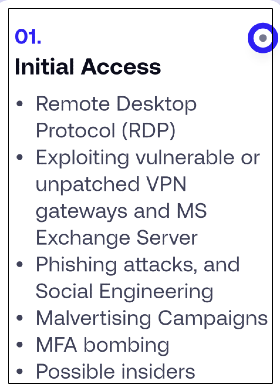

Unauthorised access, not using zero-days, is gained by forcing an error on our side.
Examples include, clicking on phishing links, reusing passwords (for a compromised account), not installing software updates and unnecessary attack surface exposure.
These are behavioural issues, better solved with training, awareness and testing.
More products, same problems?

Client's with really good security postures rely heavily on simplicity and security by design. I once had a talented CSO (chief security officer) describe his secure design philosophy to be simply "lean and mean". Complexity is truly the enemy of security.
Clients who often drift from one buzzword to the next - from one product to another - typically have one thing in common: They fail to truly understand their problem; and don't have the (right) people, processes or visibility for data-driven decision making.
For example, what controls could protect Transunion from weak passwords?
- You could perform an audit of all passwords to identify weak passwords.
- You could enable multi-factor authentication for internet facing systems.
- You could train developers/ database administrators on secure practices.
- You could have periodic penetration tests to identify all weak passwords.
- You could restrict access to authentication services to authorised sources.
Such solutions are effective - and none of the above require a new product purchase.
Keep in mind that the products (e.g., vulnerability scanners) failed to detect this issue. This may be indicative of an over-reliance and false sense of security in such controls.
Penetration testers often say that - a fool with a tool, is still a fool. You need talented, trained professionals and well-designed processes to convert products into solutions.
In the wake of a breach, ambulance chasers will push a product, as the panacea. Without any root-cause identification, incident analysis or forensic investigation? Think about that. Sadly, I only need to think back 48 hours for a prime example,... :(
Improve talent, testing & design.

Training, testing, design and awareness (intelligence) are the foundation to robust and resilient defences. It can be surprising at how resilient your posture becomes when you have all basics in place. Over and above having the basics in place - when countering any asymmetric force - intelligence is key for efficient and effective resource allocation.
Snode and our approach.
Snode Technologies does not provide cyber defence systems alone. Our clients have unlimited access to our internal training, tooling, process design and intelligence, at no additional cost.
We no longer provide cyber threat intelligence as a subscription service - since we deem it a foundational requirement for all clients. Our training includes a host of global security specialists and subject matter experts. Design and testing teams are available to clients ensuring that all new technology innovation or adoption is secure by design.
If you would like to know more about Snode - or need Snode's assistance - contact us.

