Civitas talk on simplifying cybersecurity for startups

Civitas has asked me to present to the startup community on how to efficiently and effectively implement a cybersecurity strategy. Startups selling to a corporate client, such as a national bank or telecom, are often required to adhere to strict cybersecurity governance, compliance and risk management. The sheer volume of statutory and regulatory requirements, with the need to align to best-practice frameworks and globally accepted standards can become overwhelming for a fledgling entrepreneur.
To assist the community, I'm suggesting a 3 phase approach:
- Create a custom cybersecurity framework - amalgamate your statutory and regulatory requirements; along with your selection of frameworks and standards. These may include NIST CSF, ISO 27000, COBIT, ITIL, PCI, POPI, GDPR, etc.
- Perform a gap-assessment against the framework - break the framework down into a collection of requirements. Assess the current status against the desired maturity - the criticality - and identify the key tactical activities to bridge the gap.
- Define strategic initiatives to meet future requirements - this will help you craft a cybersecurity strategy, that runs parallel to the business and technology strategies. This will include emerging technologies you plan to adopt and the associated risks.
Creating a custom cybersecurity framework
Once you have identified the various requirements across the business, you will see a large degree of overlap. To increase efficiency, you do not want to design and implement the same controls twice. An amalgamated view will empower you to meet multiple requirements - all with a single action. Let's take a look at what this looks like:
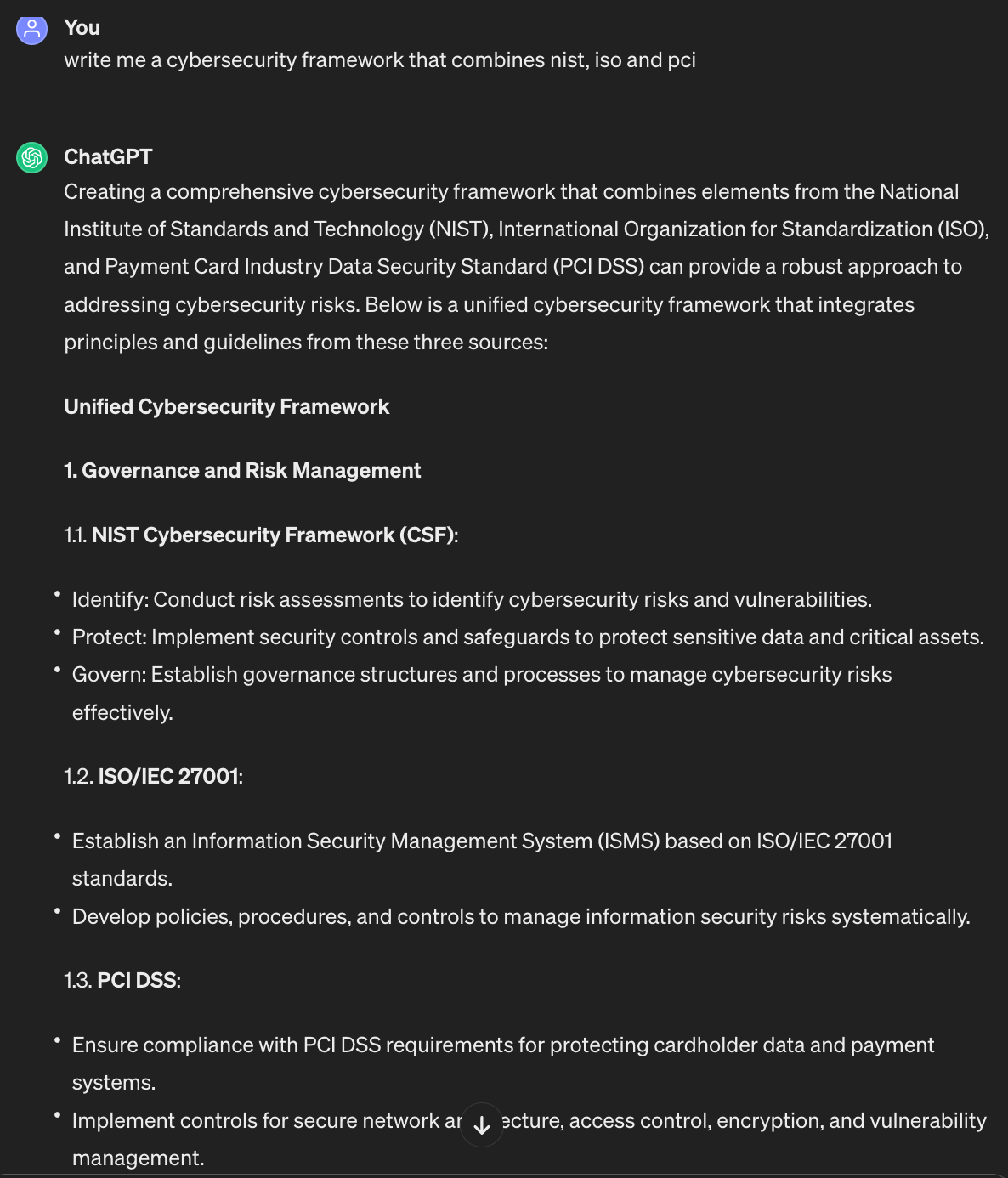
Here is a simpler consolidated view (even though the requirements are more complex):
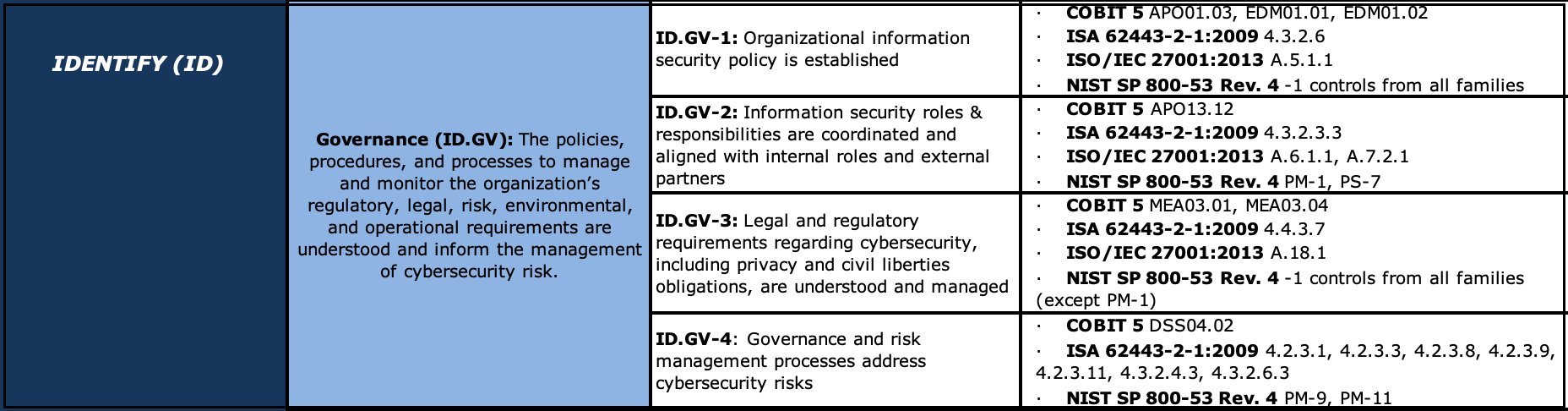
A more detailed (ISO 27001/2) view, for those who love their GRC references (not me):
If you don't know how we got here - do not worry - you can download this framework and avoid the pain of mapping all of these requirements:
Creating a gap assessment questionnaire
Once you have your framework, you can naturally progress to a gap assessment. Essentially you need to assess your current maturity against your desired maturity.
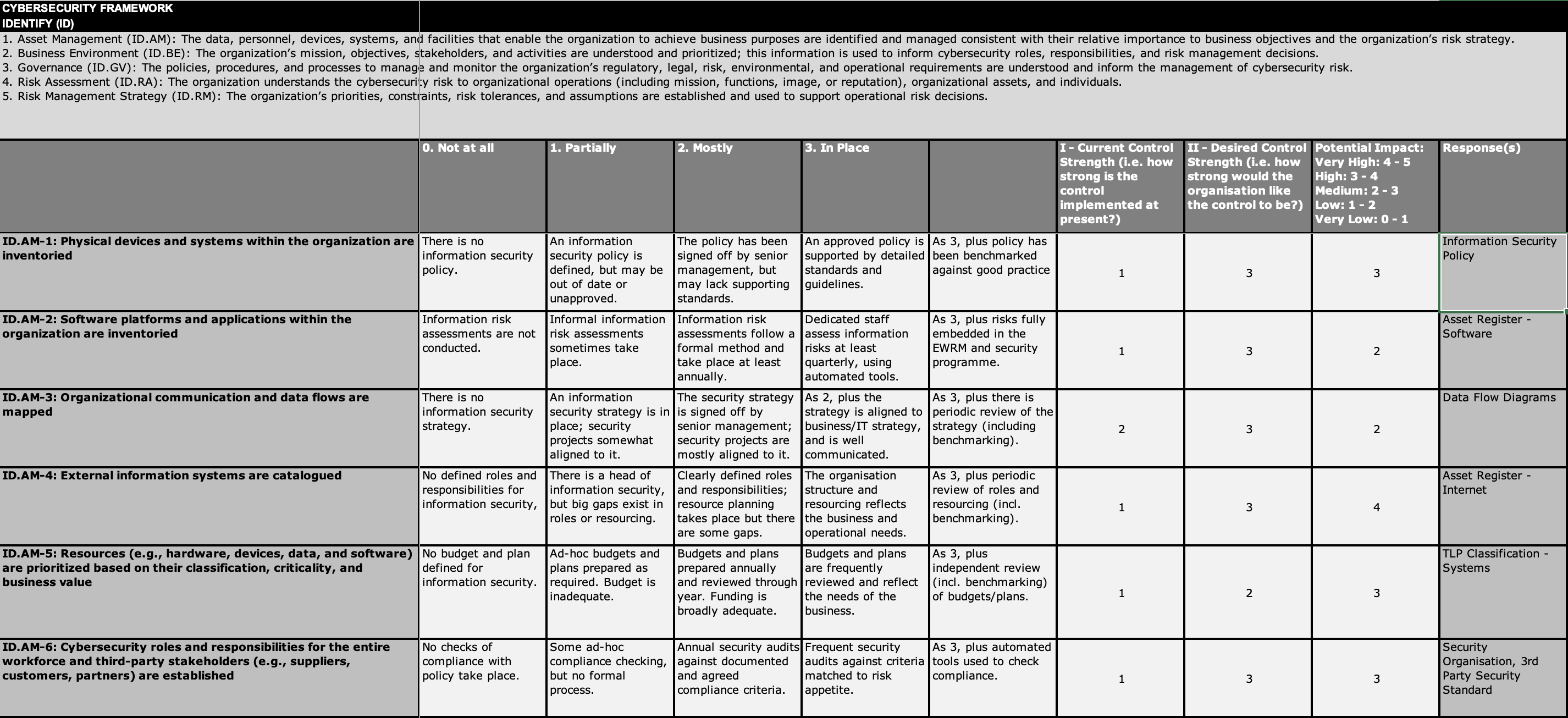
You can choose to be detailed in this assessment as shown in the extract below:
Alternatively, you can simplify your requirements into baseline objectives as follows:
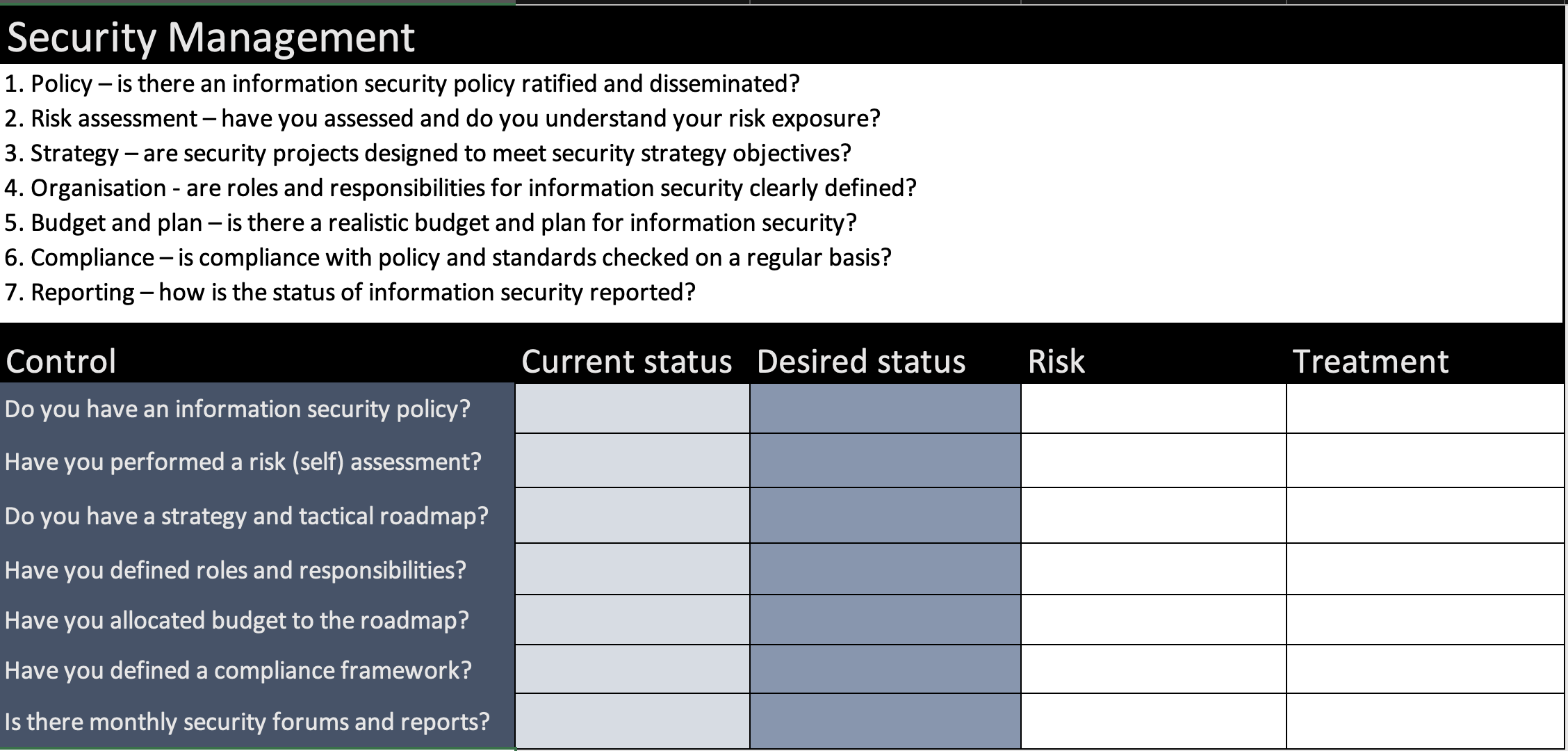
Again, to save you from the pain of creating your own questionnaire, I've provided both (including some test data - to illustrate the process to follow and level of detail to add):
Baseline standards and assessments
A security baseline standard consist of agnostic controls that can be applied across any technology landscape. It can be considered the minimum security requirement.
An example of baseline security controls for the password policy on any system:
- Enforce password complexity;
- Set password minimum age (to x);
- Set password maximum age (to y);
- Enforce password history; and
- Set minimum password length (to z).
If you can achieve (close to) 100% baseline compliance - you've done really well! Therefore, I highly recommend starting with a baseline standard and assessment.
If you are well positioned to implement technology specific standards, check out CIS:

Future and emerging requirements
These inputs are vital requiring research and foresight. There are various forces that drive such requirements, including business strategy, Geo-politics, technology innovation. Here is a list of the most common requirements our client's have included:
- Artificial intelligence - trust, bias and risk management.
- Autonomous vehicles and industrial systems security.
- Quantum and the risk to encryption (e.g., store now decrypt later).
- Metaverse, both opportunities and threats associated with it.
- 5G and low earth orbit satellite connectivity and security.
- Misinformation, disinformation and psychological operations.
For example, there is a Snode research paper on the Metaverse available here.
Formulating your strategy and roadmap
Once you have both current risk exposures and future strategic objectives, you can break it down into a risk-based tactical roadmap. A roadmap (extract) is shown below.
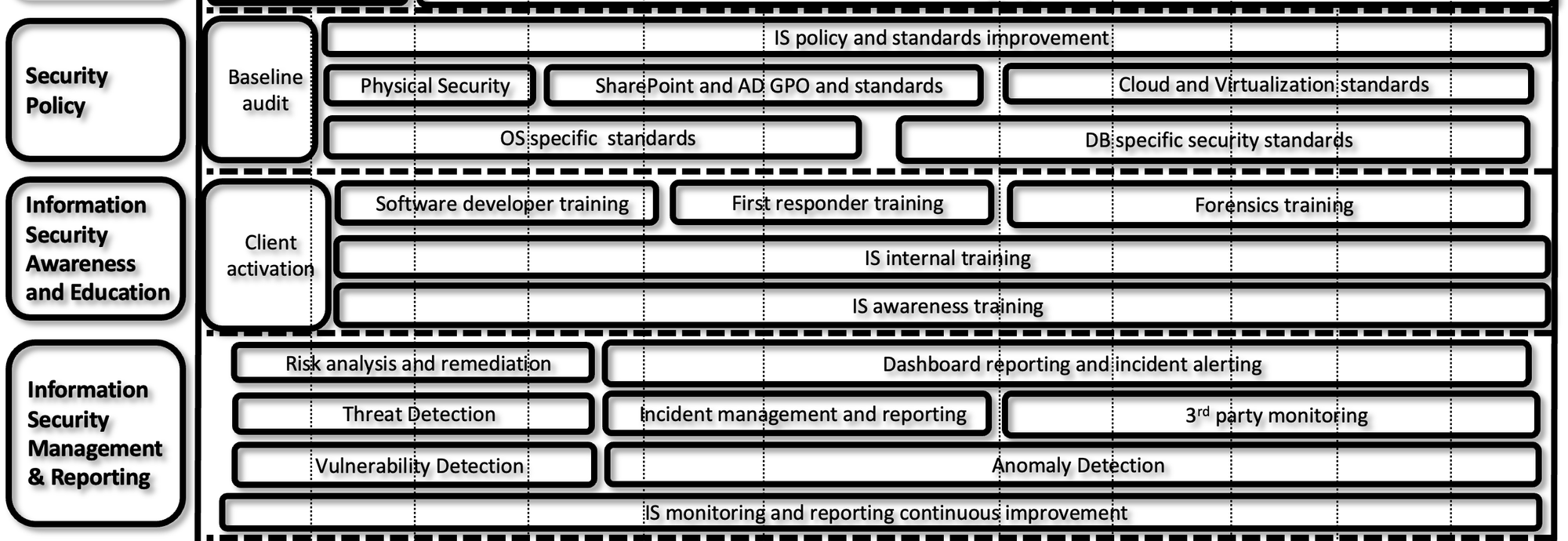
Tooling References
A list of tools to assist you with the design and implementation of your program.



