Checking my devices for malware - Part 1 - OS X

Christmas is that time of the year where I dismantle, burn and rebuild all my machines.
There are 4 operating systems that I use (as base operating systems):
In this series of posts I will cover the following topics for each operating system:
- The all important - WHY?
- Operating system check; &
- Checking for persistence.
Important to note, this is not a digital forensics or secure configuration procedure.
The all important - WHY?
If you're wondering if I run endpoint protection - I do. If you're wondering why I still need to perform these manual checks - I'm paranoid. My mantra in this regard,...

Here is a good example, of when a little paranoia goes a far way,...

If you think that this won't happen to you (or us) - think again,...

Operating system checks
This is my quick list to detect clear and present danger:
The essential mix
You first have to confirm the basic controls - I won't go into too much detail here:
- System update - this includes removing unnecessary services, creepware, etc.
- Secure configuration - this includes strong password, encryption, policies, etc.
- Security controls - this includes firewall, endpoint security, data backups, etc.
A good resource is the CIS security standard which details the most salient points.

Initialisation check
On the initial boot - I like to check five things:
- Active user directory;
- Network connections;
- Files (active) opened;
- Processes running; &
- Trace potential issues.
This process (and even some commands) will be the same across any *nix system.
We can use the man page to display online documentation for any of the utilities.
man dscl
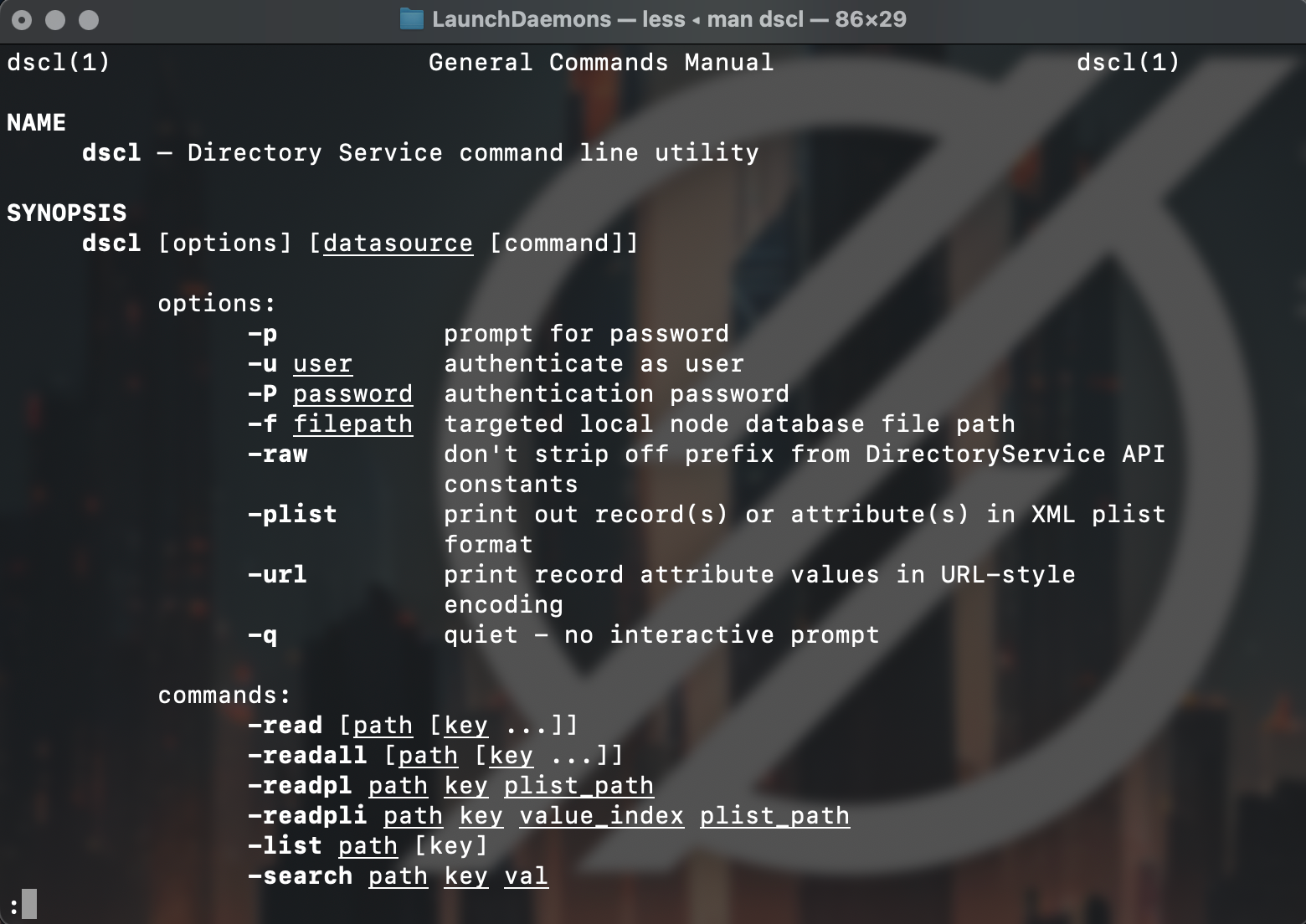
Active user directory
We can use dscl (directory service command line utility) to list all accounts:
dscl . list /Users

If you're unsure about something (e.g., nobody user account) then check it out:
We can use w and last utilities to analyse both current and past user behaviour:
w
last
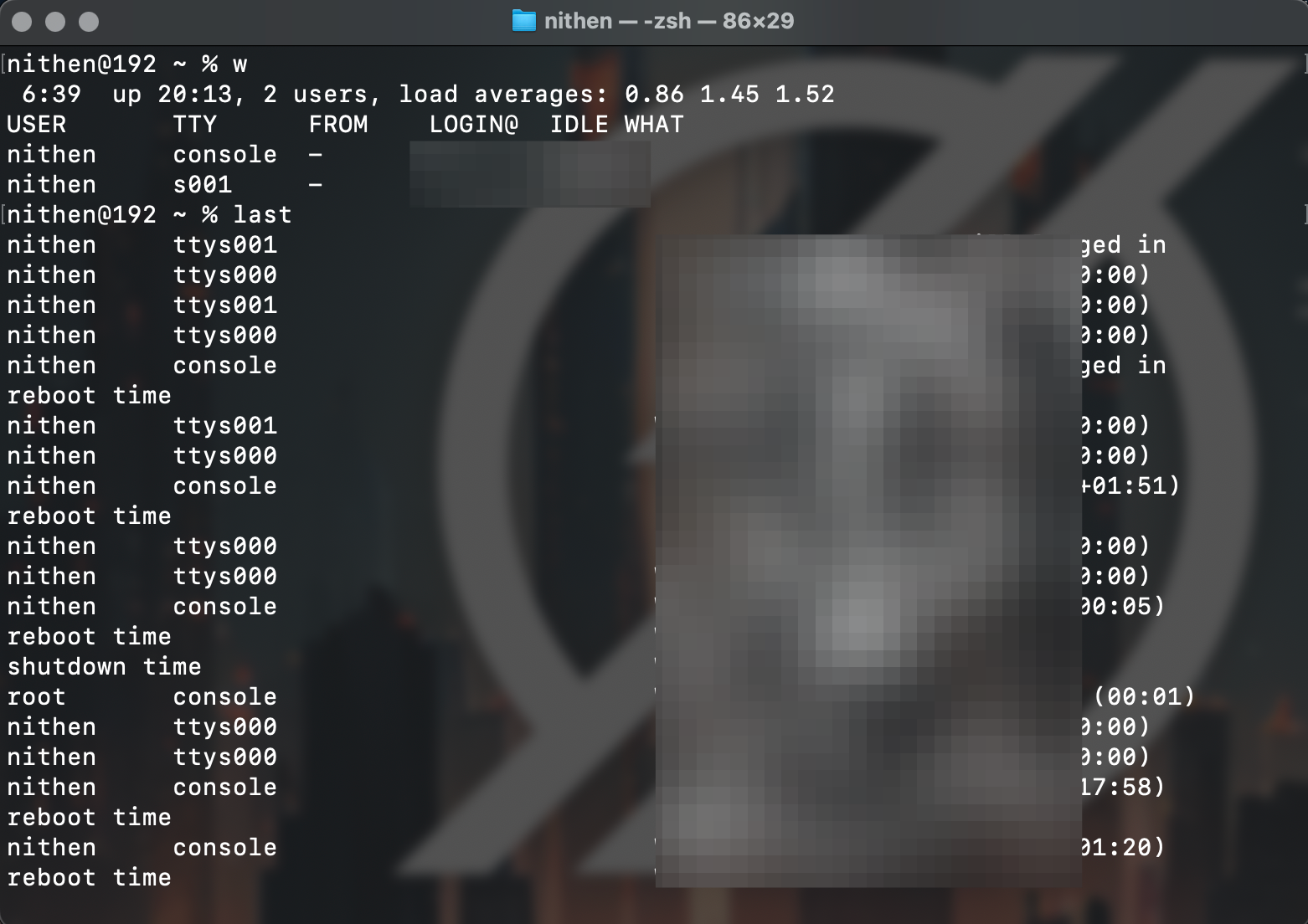
Once we have confirmed there are no signs of malicious activity - we can move on.
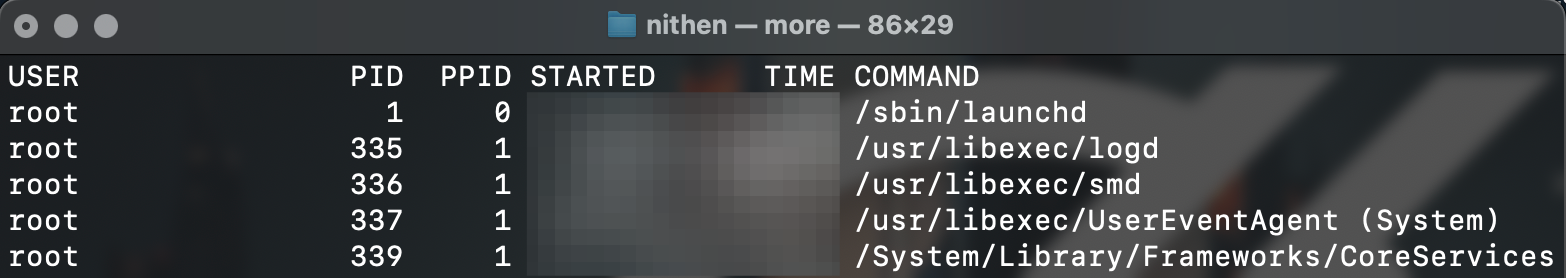
Processes running
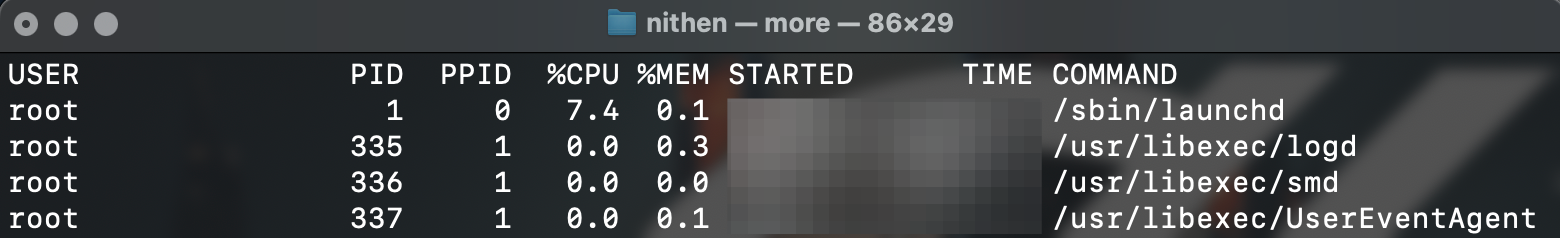
We use ps (process status utility) to analyse all running processes on the system:
ps -axo user,pid,ppid,start,time,command
You can also see the memory and CPU (central processing unit) utilisation using:
ps -axo user,pid,ppid,%cpu,%mem,start,time,command
Alternatively, use the top utility to see real-time system memory and CPU usage:
top
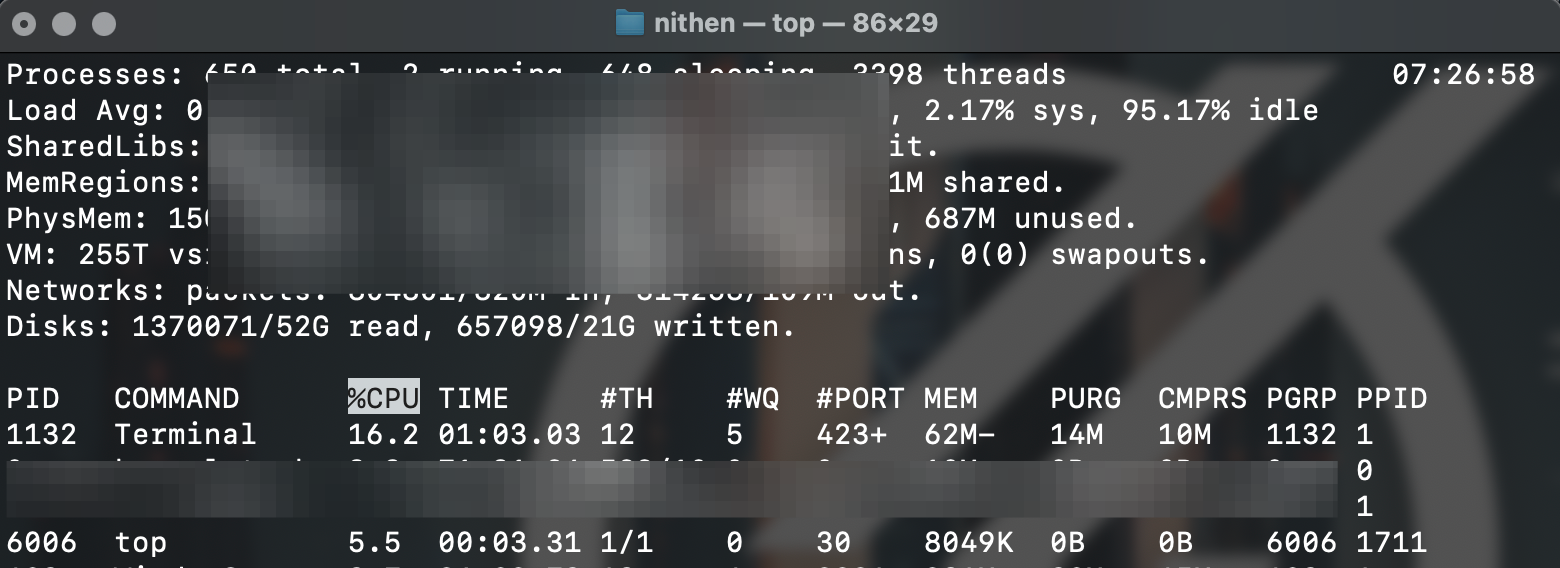
Let's say something catches your eye - like the process below (spidey senses tingle).
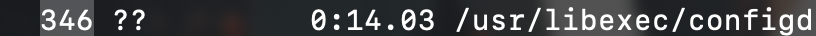
Well let's check it out,... let's check if it's signed and where it launched from,...
sudo launchctl procinfo 346
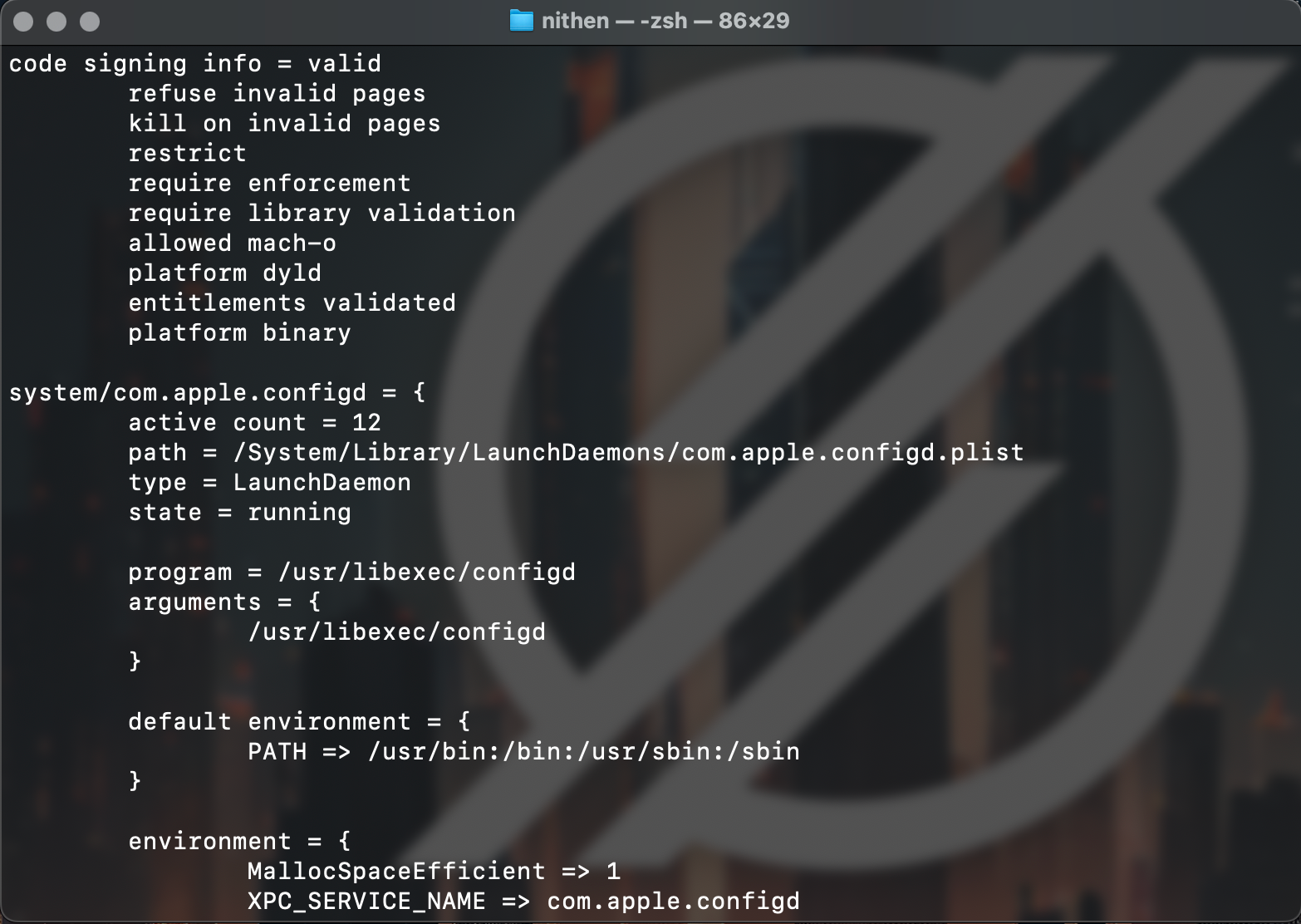
We can use ktrace (debugging) to analyse all system calls made by an application.
Network connections
Next, check network services exposed and any potentially malicious connections.
netstat -an | more
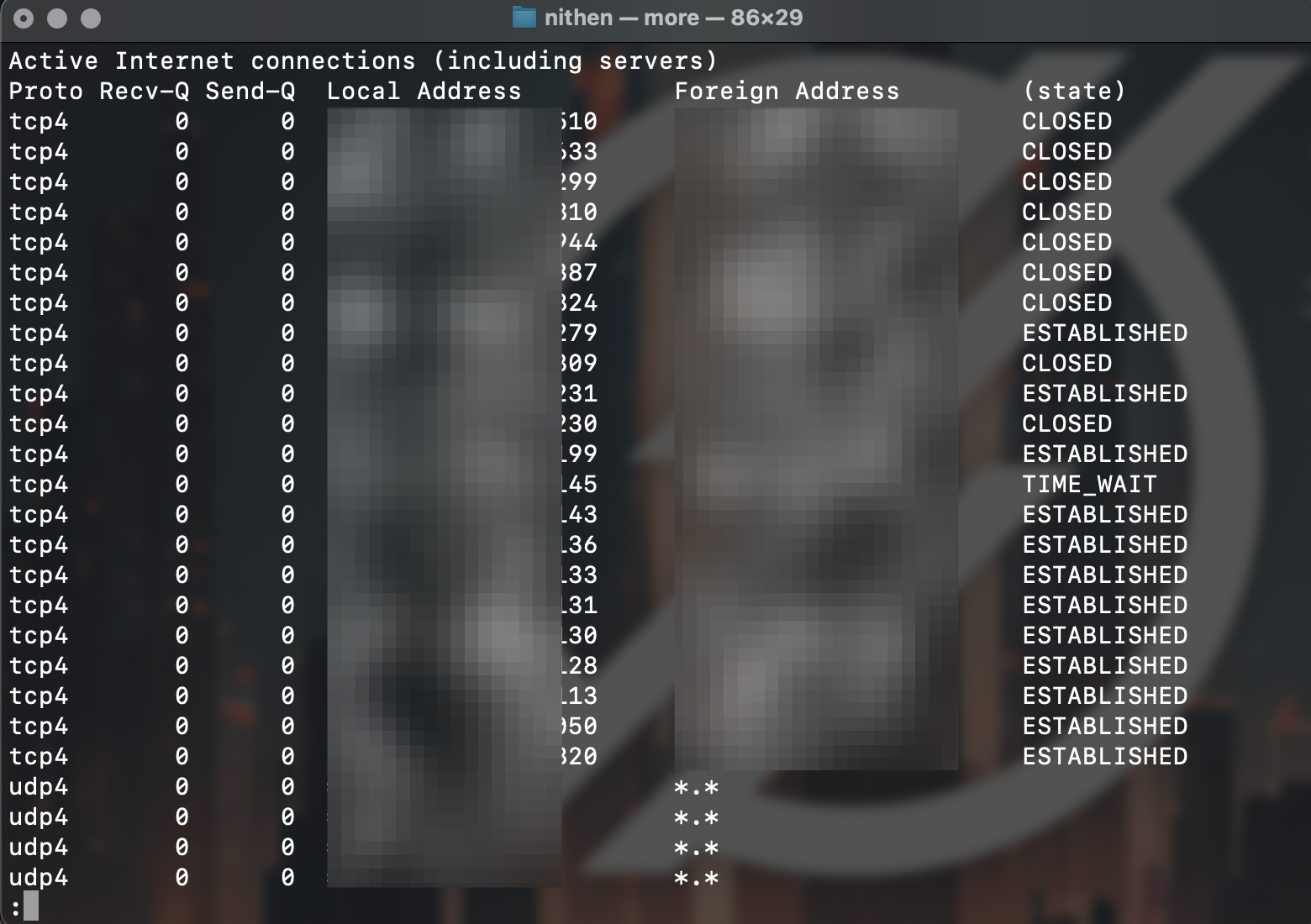
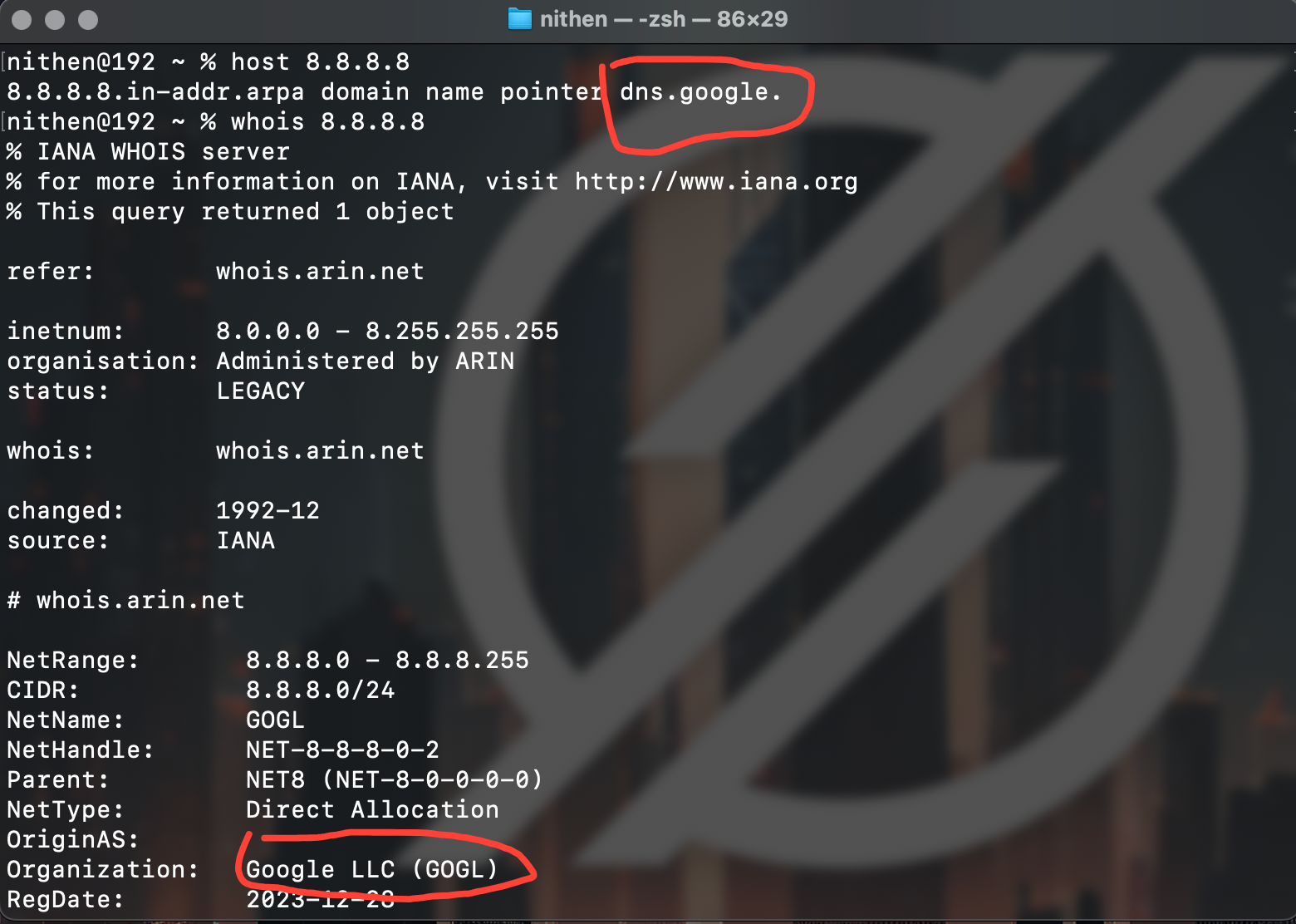
Again, if you see something you're not sure of - just confirm it with a quick check.
host 8.8.8.8
whois 8.8.8.8
Open files
To map or trace services and processes use lsof. It (lsof) lists the file handles open.
lsof
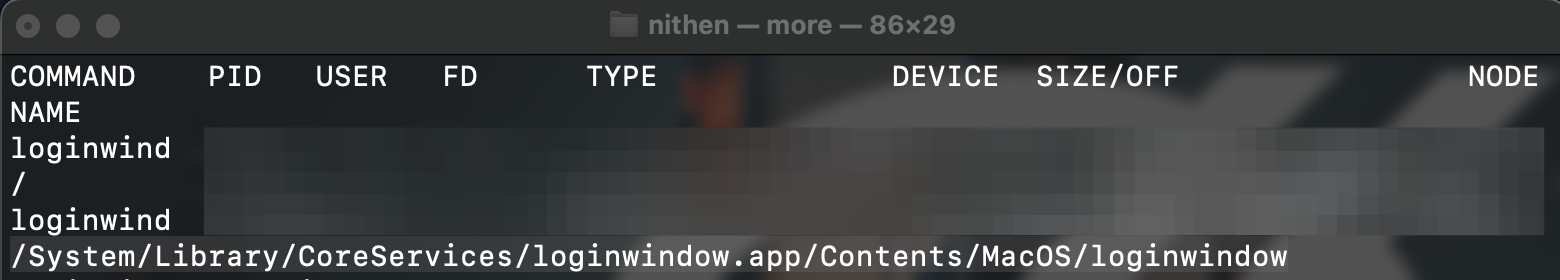
Again, if you're unsure what something is - check it (from an authoritative source).
You can also use the -i option to select internet files or sockets.
lsof -i
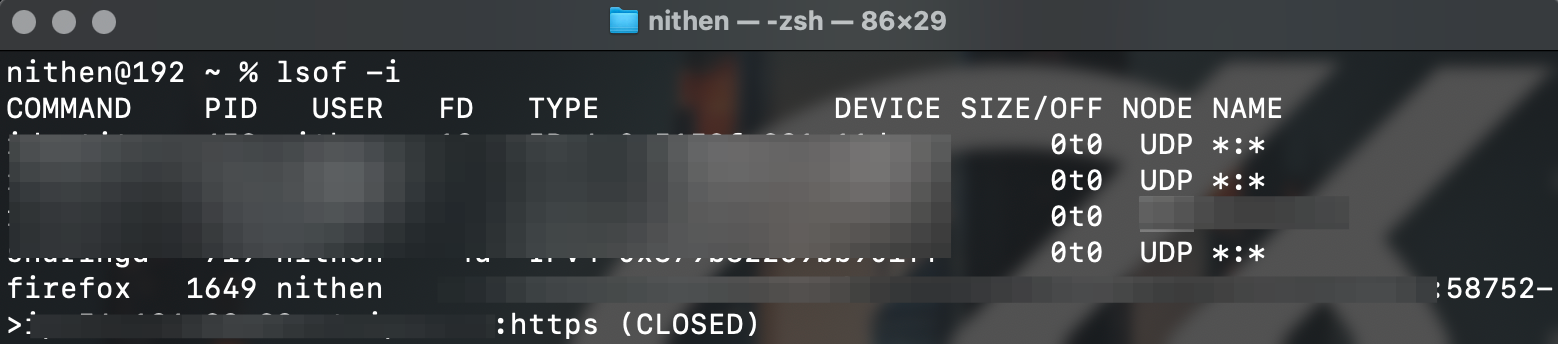
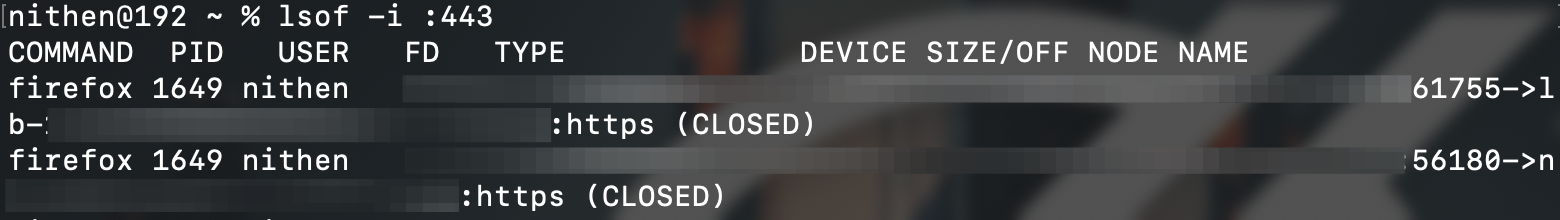
You can go a step further and filter by protocol, IP address and even port number.
lsof i :443
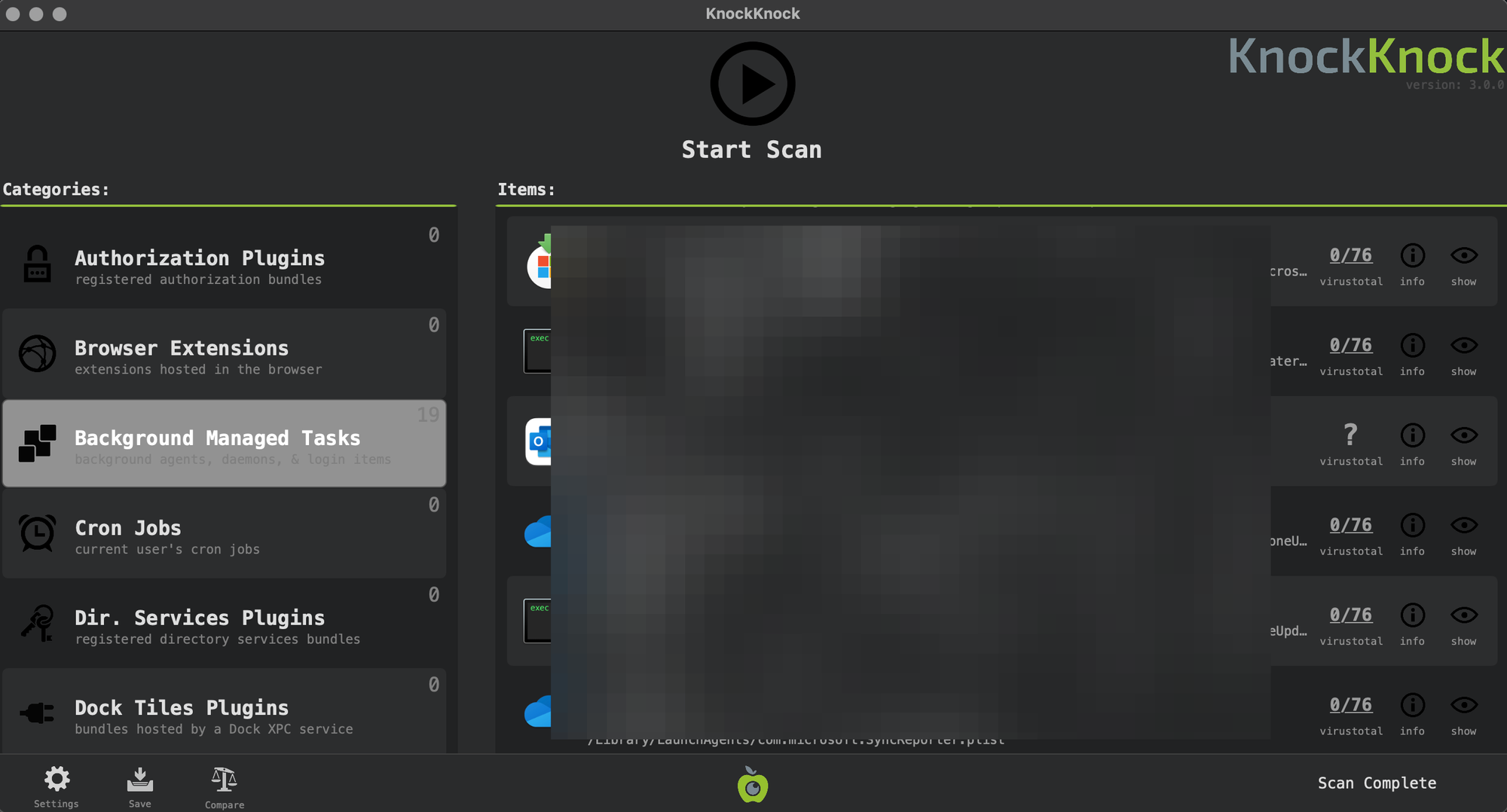
Checking for persistence
Persistence is simply how malware ensures it remains active on an operating system.
There is a great resource from the book "The Art of Mac Malware" by Patrick Wardle.

This is Chapter 2 from the book, hosted on Patrick's website, covering persistence:
https://taomm.org/vol1/pdfs/CH%202%20Persistence.pdf
You can then download KnockKnock to help you process persistence checks.
Conclusion
This is the quickest and easiest way that I have to check for any malicious indicators.
I often run tools like Snort, OSquery and Zeek alongside my (commercial) endpoint protection suite. I highly recommend it as a learning exercise, since it never fails to produce interesting results.


